Gordon Welchman
Today
13
Danger Signals
INTRODUCTION
More than thirty-five years have passed since victory in Europe in summer 1945. For me personally it has been a long and roundabout journey from my last task at Bletchley to my recent activities. At the end of the war, Bletchley Park was a flourishing and highly successful activity. It had been given all the funding needed for its many wartime objectives. And the planning problem with which Travis asked me to help in 1945 was to keep the organization alive and effective in peacetime, when objectives would be of less obvious importance and funding would be hard to come by.
At that time we and our British allies* had a long, bitter, and difficult war behind us, its lessons fresh in our memories. We had learned what did and did not work in conditions of combat. Some important aspects of the war had to be kept secret, but on the whole we were in reasonably good form to think about ways to keep our wartime capabilities alive and effective in peacetime. In the thirty five years since, however, we have forgotten much—and we have gained little (if any) new experience to improve our understanding of what war could demand of us. (The actions in Korea and Vietnam tended to teach us, how war ought not to be fought—and have left us divided and uncertain about our goals.) We are far less able than in 1945 to think positively about the capabilities for war that we should be developing. Unpreparedness now is likely to be more disastrous for us than it has ever been in the past.
* Along the way from 1945 to 1981 I became an American citizen. So, instead of talking (about “we” (the British) and the Americans, I will now talk about “we” (the Americans) and the British.
This issue did not directly concern me until I joined the MITRE Corporation in 1962. My first postwar job was in the world of department stores—a far cry from Bletchley activities. In 1948 I emigrated to America and became involved in computers and information technology. When I joined MITRE, however, I embarked on a series of military studies that, over eighteen years, deepened my understanding of the defense problems that face us, and gave me increasingly grave concern about our unreadiness to cope with them.
My knowledge of war was derived from my Bletchley Park experiences. Later, I studied shortcomings in the communications of the North American Air Defense Command (NORAD), which at that time were quite incapable of surviving an attack by nuclear missiles. Next I worked on capabilities for fighting limited wars outside Europe with conventional (nonnuclear) weapons; this phase led to the concept of a battlefield communications system that would meet the requirements of combat forces and their commanders. I switched in 1971 to a series of studies of the threat to NATO posed by the conventional forces of the Warsaw Pact. Finally, in 1978, I came back to communications, working on security measures for a revolutionary system of tactical communications that was being developed with support from the U.S. Army, Navy, and Air Force.
These assignments made me an informed, and I am afraid a rather disillusioned, student of several vital aspects of our military posture. It has convinced me that our national defense is in shockingly bad shape. We are not well prepared as a nation to fight any kind of war. We are utterly unready to deal with the nonmilitary threats with which we may be faced, though these may be just as significant as the military dangers, if not more so. We have failed to learn from history, we have failed to recognize the implications of change, and we have been doing a very poor job of anticipating the future. The handwriting on the wall is clear. It spells DANGER.
In this part of my book I will draw on my experiences at Bletchley Park and at MITRE to talk about what is wrong today and what I believe needs to be done. My experience does not cover every defense problem, but it is broad enough to demonstrate that we are in a very serious predicament,, In one area, that of communications security, I am in a unique position. Because I was in on the beginnings of Hut 6, I know more than anyone else about why the security of the German Enigma traffic broke down. Then, in 1978, 1979, and 1980, I learned a good deal about the as-yet-unsolved problems of providing both security and flexibility for the future battlefield communications capabilities that we so badly need. Thus I can see this crucial problem, as it were, from both sides.
I am convinced that our tactical communications constitute a glaring gap in our national defenses. In our craze for technological achievement in weapons systems we have put the cart before the horse.
With this in mind I shall have good deal to say about bridges between the past and the future, about changes in military doctrine that may be on the way, about the type of battlefield communications we need, and finally about matters of secrecy, security, and survival. I will start with a review of the danger signals I have seen during the last nineteen years.
NORAD
My first NORAD assignment at MITRE in 1962 revealed several dangers. A system designed for one particular threat had not been modified when that threat subsequently changed. Far too little attention had been given to the survivability of the communications on which system performance was entirely dependent. Also, system planning had been compartmentalized, and there was a marked lack of overall coordination based on total grasp of the problems involved. The necessary collaboration among all fields of expertise that could contribute to a solution had not been achieved. At first we, could not make contact with NORAD’s operational commanders, to learn the true nature of their problem. And even at the end of our study, the rigidity of military procedures still prevented direct contact with the NORAD high command. On balance, however, this first exposure of our failures in military planning did not disturb me nearly as much as my later studies. When we were through with the NORAD study, it did at least appear that remedial measures were under consideration.*
* I hope the reader will pardon the acronyms and jargon that follow. These are the terms our military establishment uses to discuss its systems and its organization. Once one gets acclimatized to them, they are not all that bad. Any attempt to translate into ordinary language might well be even more confusing.
Our first large-scale computerized defense system was known as SAGE, for Semi-Automatic Ground Environment. It was aimed at the defense of the United States and Canada against the threat of Soviet bombers carrying nuclear weapons. The NORAD system was based on regional commands, each of which had a number of SAGE control centers whose radar and computer equipment were to follow the tracks of enemy bombers and be able to direct attacks on them by our intercept aircraft. Early warning of impending attacks by enemy bomber formations was to be provided by a variety of forward radar installations. A teletype network, known as SURTAC (for Surveillance and Tactical), allowed formatted digital messages to be passed among the forward facilities, the control centers, the regional command posts, and the headquarters of NORAD’s Commander in Chief, CINCNORAD, at Colorado Springs.
By 1962 the threat of attack by nuclear-armed ballistic missiles had become a reality, and a Ballistic Missile Early Warning System (BMEWS) had been put into operation. It was thought that an attack by Soviet bombers would be preceded by a missile attack, the first salvo of which could well knock out CINCNORAD’s headquarters.**
** Indeed all the SAGE facilities in the United States were “soft,” or vulnerable to nuclear missile attack.
When I came into the picture, plans were going ahead for a “hardened” underground facility for CINCNORAD. The Canadians had already constructed an underground headquarters for the North Eastern Region, for which they were responsible. A system was sought that would allow the hardened Canadian facility to act as an Alternate Command Post (ALCOP) if CINCNORAD’s headquarters became inoperative. MITRE was asked to establish Project SNOCAP (Survivable NORAD Capability) to look into the matter. At first I was in charge of the communications aspects of the study; later I became project leader.
It was worrying to find that little attention had been paid to the survivability of the communications on which everything depended. If one of the BMEWS sites had detected a missile attack, it would have been extremely important to get the warning to the national command and to the strategic air command immediately. Yet these commands could only get such warning from CINCNORAD (which might be knocked out by the first strike), and each BMEWS site had only one primary communications channel to CINCNORAD, a channel that frequently failed.*
* This was a high-capacity channel designed to carry raw data for processing by a computer at Colorado Springs, even though each B.MEWS site had its own computer, capable of processing the raw data. When the primary channel failed, the warning to CINCNORAD, derived in that case of necessity from the B.MEWS site computer, would be sent by voice. If voice communications failed, the warning could be sent by teletype. In fact the need could have been met at far less cost by teletype circuits with switches to carry the warnings directly to all the places where they were urgently needed, including the Canadian ALCOP we were studying. Moreover, because teletype circuits are relatively inexpensive, it would have been possible to provide redundant circuits and switches that could come into operation if and when the normal routing of messages failed.
The SURTAC teletype circuit network, leased from public utilities, ran through areas that could be regarded as prime targets for a missile attack. In fact the communications network on which the SAGE system depended could well have been put out of action by missiles before the Soviet bombers arrived. Working closely with a Canadian communications engineer, we prepared a plan that would reroute teletype circuits to avoid prime target areas and provide alternate routing between any two terminals. It was disturbing that no such steps had been taken before our study.
NORAD’s telephone circuits were also leased from public utilities, but we soon found that the NORAD people had done far less to ensure survivability under nuclear attack than had the AT&T planners of the public telephone system, who were doing a very good job. Each of the many agencies and organizations involved in the operations at NORAD headquarters had been demanding its own separate dedicated telephone lines, which made it prohibitively expensive to provide redundancy. It was gradually being accepted that far greater survivability, and equally good service, could be obtained by a common-user voice communications system employing enough circuits and switches to provide many alternative paths between any two terminals. This was the birth of the present AUTO VON (Automatic Voice Network) system in the CONUS (continental United States). Still, however, system design had not taken account of the threat of sabotage. At some switching centers and relay stations military circuits were on the same racks as commercial circuits. The military circuits were colored red, to facilitate restoral, but this also was extremely helpful to any potential saboteur, who would at once see which wires to cut!
By the late 1970s CONUS AUTOVON, linked to the AT&T system, had nearly seventy switching centers and was thought to possess considerable survivability. But technicians who worked for several years on the installation of the similar European AUTOVON system for NATO stated categorically that this communications network could not survive a massive attack by conventional Warsaw Pact forces—which would undoubtedly make use of sabotage. Thus, some fifteen years after the SNOCAP period, a system designed to serve U.S. forces in Europe and to connect them with the CONUS was not survivable. Furthermore it provided little traffic capacity. So little, in fact, that a study concluded that if a random 90 percent of the West German commercial toll network were knocked out, it would still work better than a fully operational AUTOVON in the same area.
As I have noted, in the first phase of SNOCAP, we could not make contact with NORAD’s operational commanders. Instead we had to accept the description of the ALCOP problem given us by a few staff officers who did their best to guess what their chief would think. In their anxiety not to do anything of which he might disapprove, they gave us rigid guidelines that proved to be absurd. Largely because some of the stated requirements were unrealistic, we designed a thoroughly bad system. Fortunately General Muehleisen, a NORAD regional commander who had been acting as Alternate CINCNORAD for some time and had thought deeply about his task, got wind of our proposed system. He made a personal trip to Colorado Springs and convinced CINCNORAD that the restrictive requirements must be removed and the system redesigned.
At that point I became project leader. I was allowed to take my whole group for a week to General Muehleisen’s regional command center, where we made contact with all sections of his staff. The general put on an exercise for our benefit. I myself was able to spend a lot of time with his deputy, learning about the functions of an operational commander. For this was a real live situation: Every day there would be tracks of unidentified aircraft to investigate; many of them would be tracks of Soviet planes. Continual vigilance was needed.
We spent a week at the hardened regional command center in Canada, where the commander and his staff were willing to discuss what would be involved in taking on ALCOP duties as well as those of a regional command post. Armed with a far better grasp of the problem, we were then able to come up with a workable system. When this was presented to CINCNORAD, we were told that “never had so many generals agreed to anything so quickly.”
This of course was gratifying. However, our proposed system was not implemented—for a variety of reasons, some good, some bad. The political implications of putting the only survivable NORAD command center in Canada were obviously a serious concern, and may well have been the basic cause of the rejection of our proposals.
I personally had learned a great deal, however. It had been an unusual opportunity to discuss problems with operational commanders and their immediate staff. But the handling of our presentation to CINCNORAD revealed a serious malaise of our peacetime military establishment. CINCNORAD was not prepared to listen to a presentation by a civilian. Our proposals had to be presented to him by someone wearing the uniform of an officer in the U.S. Air Force. In our case fortunately this did not matter, because the Air Force officer supervising Project SNOCAP had worked closely with us, had contributed a great deal, and was well able to present our ideas. But in principle it was bad. It was an example of a serious fault of peacetime military establishments, which tend to be “role oriented” rather than “task oriented.” They are more interested in having things done in accordance with established procedures than they are in the successful accomplishment of a task.
LIMITED WAR ENVIRONMENTS
Early in 1964 I was transferred to a department that was studying air operations on a conventional battlefield outside Europe. I was to study offensive missions against ground targets. My department head was seriously concerned that everyone seemed to be thinking about what happened at command posts. There was too much talk of using computers. I was asked to concentrate on what was involved in the actual attack. I soon ran into more danger signals. The higher levels of our military establishment were paying far too little attention to the individual characteristics of the different types of limited war in which we might become engaged. Imaginative thinking was suggesting changes, but the establishment was not responding.
In the early 1960s, for example, during John F. Kennedy’s presidency and for some time after his assassination in November 1963, realistic consideration was being given, at the national policymaking level, to three broad issues. First was the need to identify the different kinds of war in which U.S. forces might have to fight. Next, the need for military policies, procedures, a procurement appropriate to all the different situations had somehow to be met. Lastly, special emphasis had to be placed on what the Communists call “wars of liberation,” which they had selected as their primary method of attack on the free world. But this period of realistic consideration, although it produced some very good thinking, did not lead to appropriate action. Established military doctrine was unaffected, as were the aims of military procurement.
When, in early 1964, I was starting to think about air attacks on ground targets, I was also asked to prepare an analysis of future limited war environments, which I completed in summer 1964. I found plenty of help in earlier studies, and plenty to worry about. In 1957, for instance, the Military Review had published two articles on “readiness for the little war” by a group of eight U.S. Army officers, all of whom were members of the faculty of the U.S. Army Command and General Staff College. They concluded that:
The United States does not have a highly mobile military force in being that gives us the capability of immediately retaliating against small-scale Communist aggressions on a graduated retaliatory basis. Small aggressions do not warrant big bombs.
They recognized that the mobile force would require a political as well as a military capability; it would include and utilize the capabilities of all services; and it would be capable of participating in, as well as augmenting, indigenous capabilities in the conduct of unconventional warfare.
Another example of the increasing concern about the rigidity of military thinking was an article in the Military Review of May 1960 entitled “Dual Strategy for Limited War,” which stated:
Americans should study the Communist campaign which was waged in the Philippines because it may be a harbinger of a type of warfare to come, a classic example of one type of limited war. In addition it should be studied because Magsaysay won his war and thus became the only democratic leader in Asia, and one of the few in the world, who for all intents and purposes completely defeated an overt Communist armed rebellion in his country.
Today, who remembers Magsaysay and his “dual strategy,” which was essentially a blending of military actions with political reform and aid for the people? Yet in 1964 this chapter of history seemed to me to be of great importance. Greater attention to it might have made a big difference in Vietnam.
Another source I found helpful was Seymour Deitchman’s Limited War and American Defense Policy. Deitchman points out that terrain and climate will govern both the mobility of the ground forces and the size of each ground force that can operate as a coherent unit. From his geographical studies Deitchman deduces that, outside the highly developed areas of the world, wars will be fought by armies organized in relatively small units. In underdeveloped areas, unconventional warfare is likely to be an important, if not a dominating, element in any war. Indeed in the early 1960s there was much talk of counterinsurgency, or COIN.
Using ideas from such sources as these I did my analysis in what seemed a very obvious and straightforward manner. With help from the Foreign Technology group in the Electronic Systems Division of the U.S. Air Force Systems Command, I listed the most probable trouble spots around the world. For each of them I reviewed:
Political-military considerations
Types of warfare and terrain
Enemy capabilities
Air mission requirements
Principal capability developments needed
The analysis was accepted and used immediately in an Air Force advanced planning document called, I believe, “The Five-Year Plan, 1964.” It was also used in a “master plan” for an advanced tactical air control capability, prepared in MITRE and published in April 1966. It was used again in the report of a Vietnam study group with which I became involved, probably in late 1966. In fact my analysis, completed in a few months by a newcomer to tactical advanced planning, seems to have been treated for some years as an authoritative statement on limited war environments! I find this far more worrying than flattering. Why had no such document been prepared before 1964? Why was it not revised for the master plan and the Vietnam study?
One can only conclude that there was no serious Air Force interest in the characteristics of possible future wars. This is a real danger signal. How can we hope to be well prepared if we are not willing to study what we should be prepared for? Moreover, my analysis, though derived entirely from open literature, was classified. Other students of limited war would thus have difficulty getting access to it. They might not even hear about it.
PRESIDENT KENNEDY’S CALL
In September 1964 I attended a course at the Air Ground Operations School at Eglin Air Force Base in Florida. The AGOS course was concerned with the system that had been designed to control direct air support to ground forces in battle. That system seemed to me unnecessarily clumsy and complicated. I had the feeling that the officers in charge of the course felt so too, and that something better was needed.
For me the most interesting part of the AGOS course was a visit to the Special Air Warfare Center (SAWC), where the 1st Air Commando Wing had been activated on June 1, 1963. This was part of President Kennedy’s response to his meeting with Khrushchev in May 1961, in which the latter predicted the triumph of Communism in the new and less developed countries as a result of wars of liberation supported by the Kremlin. In a special message to Congress on May 25, 1961, the President said that our special forces and unconventional warfare units would be increased and reoriented. Throughout the services new emphasis was to be placed on special skills needed to provide efforts short of open conflict but necessary to counter Communist-sponsored guerrillas or insurgents. In the same special message Kennedy stated that assassins had taken the lives of four thousand civil officers in the last twelve months in South Vietnam. The war of liberation in that country was already in full swing.
Working closely with U.S. Army Special Forces teams, the air commandos of 1964 were trying to help the South Vietnamese fight their own war. I was able to talk with commandos who had been working with the South Vietnamese in those early days. The Commander at SAWC (General Pritchard, I believe) was frustrated because he could not persuade the authorities to put money into production of new simple aircraft. Even the OV-10, originally designed for counterinsurgency, was, in his opinion, far too complicated for use by not-very-well-trained Vietnamese pilots.
Another worrying aspect of that day at SAWC was the antagonism of an Army officer on the AGOS course to the air commandos. He considered that they were doing a job that should be done by the Army Special Forces. At the same time he did not seem to be happy about having Special Forces in the Army. He was a tank man, and may have thought that fighting without tanks is for the birds. Anyway, this sign of friction between branches of the service was disturbing. Perhaps the effect of President Kennedy’s May 1961 call to Congress for a revised doctrine was already beginning to fade; later on it disappeared completely.
In March 1965 I visited R. F. Futrell, Air Force Historian at the Aerospace Studies Institute, Air University, Maxwell AFB. He had written The United States Air Force in Korea, an extremely valuable book. I found that there had been a strong response to President Kennedy’s call for new doctrine to meet changing threats. In 1962 the Concepts Division had started a study program to examine the role of airpower in guerrilla warfare. Lessons were to be drawn from the many small wars that had been fought since World War II. I talked to a colonel who had just completed the seventh study in the series, “Guerrilla Warfare and Airpower in Algeria.” This was particularly interesting because it described a highly effective organization of joint air/ground operations, supported by an extremely effective method of achieving rapid information exchange with small units scattered all over the country.
I also talked to an officer who was completing a year’s research on the problem I was studying at the time—air attacks on ground targets in various types of warfare. We had both concluded that Air Force doctrine on the matter was far too rigid. Futrell helped me by criticizing my draft report on the subject and allowing me to browse through official reports from Vietnam. He also lent me a copy of a valuable but hard-to-get analysis of U.S. Tactical Air Force operations in Europe. Many of its recommendations have been ignored, though they were made by the commanders who had actually carried out the air operations in support of ground forces.
The activities of the air commandos in Vietnam were being taken very seriously at the Air University. A special course was being given for Air Force personnel assigned to duty there. The course was described to me and I thought it was absolutely first-rate. At the time of my visit the Aerospace Studies Institute was, I believe, regarded as a source of new doctrinal ideas. It seemed well able to exercise this function. However, as I understand it, the establishment in Washington disapproved of this arrangement and transferred all responsibility for doctrinal studies to Air Force headquarters in Washington. The promising attempt to modify doctrine in the light of innovative thinking and imaginative pictures of different types of future wars was killed.
In the early days of Vietnam few people were aware of what was going on, so the story is obscure and difficult to trace. But it needs to be dug out, because it illustrates a danger that we face today. People have a tendency to filter out what they do not want to hear. Before World War II, an appeasement-minded government in England filtered out the information on Hitler’s Germany that they were receiving from their Secret Service. The British, French, and Americans took no notice of the German theory of tank warfare that was published in open literature by a German, Max Werner, in 1938. During the Korean War General Mac Arthur chose to ignore Chinese public statements of their intention to intervene, and received a rude shock, costly in American lives, when Chinese General Lin Piao sprang his trap. In the early days of North Vietnam’s subversive activities in South Vietnam, we did not listen to clear evidence of what was going on.
In 1961 General Vo Nguyen Giap, the North Vietnamese commander, published his book The People’s War—The People’s Army. He explained his concept, largely taken from Mao Tse-tung, of the three phases of a war of liberation: guerrilla warfare, mobile warfare, and the final offensive.
The preliminary phase would start at the village level with the arrival of specially trained commissars from North Vietnam. In each village the commissars would convince the population that their troubles were due to their own government. They would wait until the assent of the majority of the village inhabitants had been won. Then the commissars would ask the people of the village to indicate the traitors and government agents among them. Assassination committees would be entrusted with carrying out executions. Guerrillas would be recruited. The village would become a paramilitary base, capable of bringing effective aid to regular units in the later phases of the war.* General Giap even explained a weakness of this kind of war: that, if the mobile stage does not continually expand, it will dwindle back to guerrilla warfare, which will ultimately peter out.
* The details of the preliminary phase were published in the New York Times, August 16, 1 9 6 4, by Max Clos, a correspondent for he Figaro, under the title “The Strategist Behind the Vietcong”
President Kennedy was doing his best to exploit the weakness that Giap himself had pointed out in his concept of the “people’s war.” The President wanted to help the South Vietnamese prevent expansion of mobile warfare, so that operations would indeed dwindle back to guerrilla warfare and peter out. But how many people know about this early phase of U.S. involvement in Vietnam? It never hit the news because, after President Kennedy’s death, “tradition” became dominant. The regular troops of North Vietnam came into the picture, as did those of the U.S. Army. The whole nature of the war changed, and unfortunately it is this second phase that most of us remember.
The history of the area was distorted in the public mind, and not insignificantly by the leadership in Hanoi, which was deliberately trying to attack the minds of the American people—with considerable success. A strong feeling grew up, particularly among young Americans, that our involvement itself, rather than its manner, was wrong, and that North Vietnam had right on its side. In recent years the same young people who were influenced by this propaganda have been coming round to the opinion that the North Vietnamese are a ruthless nation, whose expansionist ambitions and general callousness should not be condoned.
The true story of the earlier history of South Vietnam (which was once the independent country of Champa), North Vietnam, Laos, and Cambodia, though fascinating, is hardly a subject for discussion here. But it is worth making the point that North Vietnam’s deliberate influence on the minds of the American people is a type of clandestine warfare against which we should be continually on guard.
MASTER PLAN OF 1966 AND VIETNAM STUDY
I mentioned that my 1964 analysis of limited war was used in a “master plan” for an advanced air control capability completed at MITRE in April 1966. My own contribution was a proposal to improve our ability to attack ground targets by providing additional capabilities for an Airborne Forward Air Controller (AFAC). I want to say a little about this, because it brought me in touch with a vivid example of faults in our methods of military procurement for changing or newly perceived needs. Innovative thinking, though accepted in the initial phase, was frustrated in the end by lack of continuity in the planning process.
In October 1965 a MITRE group produced a working paper describing a new concept known then as the Airborne Electronic Grid and Information System (AEGIS). Using available technology, the system would enable some 120 aircraft operating in a battle zone to determine their positions in a common grid, to report their positions to a ground-based command center, and to receive commands from that center. The position reports were to take the form of short coded digital messages. They would be repeated in a broadcast on a single frequency so that each subscribing aircraft would receive all of them. Electronic equipment in the aircraft would present the pilot with a screen display showing his own position and the relative positions of other aircraft.
I had been studying the highly successful use of AFACs in Korea. Each AFAC, working in close touch with ground units, would spot enemy targets and control air attacks on them. It occurred to me that, with the new capability of laser ranging, an AFAC pilot could determine the position of a target and report it, together with his own position, by means of AEGIS. The target location would thus appear on the screen display of an attacking pilot, helping him to find it. Working with a MITRE engineer, Lou Williams, I developed a proposal for an Airborne Tactical Air Support Team (ATAST) that used a small two-seater aircraft.
Remember that during the early part of the Korean War and again in South Vietnam, a small low-flying aircraft could fly over enemy territory without getting shot down. Not so today. In Vietnam, in the early days, an AFAC could fly slowly at low altitude over the same bit of territory day after day and so be able to spot Subtle changes that would indicate the presence of a small enemy Unit. But, because the AFAC would be seen flying nearby, the enemy unit might guess that it had been spotted. Later in the war the AFAC, in order to survive, had to fly at much higher altitudes at much higher speeds. I am told by a pilot that, after flying over the same territory for about a month, an AFAC could still spot small targets on the ground. Moreover, because he would be observing a much wider area and would appear only as a speck in the sky, an enemy ground unit would be far less likely to know that it had been observed.
Not long after the completion of the master plan I became involved in a Vietnam study group, formed to look for ways of improving capabilities in South Vietnam. At that time we were still trying to support the South Vietnamese in something like Magsaysay’s “dual strategy,” combining military and political action. I proposed, in some detail, a countrywide organization of two-man airborne teams, somewhat similar to the ATAST, that would act as observers and controllers, keeping in close touch with the civilian administration as well as with military forces. Possibly as a result of this, Lou Williams and I were asked to spend a day at the Aeronautical Systems Division (ASD) of the Air Force Systems Command, where a group had been convened to study means of improving capabilities for nighttime operations in South Vietnam. It was part of a project called SHEDLIGHT. We found that the members of the group were all promoting weapons systems and other capabilities already under development. None of them seemed to have thought about the special problems of the small-scale dispersed operations that characterized the situation in South Vietnam at that time. Williams and I argued that in this peculiar environment our capabilities had to be coordinated by something like the well-known AFAC, but with added capabilities for nighttime operations.
After many hours of argument (the discussion lasted well into the night), the Air Force officer in charge of the study saw our point and agreed with us. He went to a blackboard and showed, from his practical knowledge, how our ideas could be improved. We had been proposing that an AFAC, having spotted a target, would control an attack by giving directions over voice radio. The experienced officer suggested that the AFAC, having spotted a target, should fly on as if nothing had happened. Then, as the attacking aircraft approached, he would return to the scene and head for the target he had spotted. The navigation problem of the attacking aircraft would be reduced to getting on the AFAC’s tail and following him—a beautifully simple and practical scheme.
The outcome of that discussion was that the need for an AFAC with nighttime capabilities (dubbed a NIFAC) was included in the study group’s recommendations. The OV-10 was selected for the mission: Its manufacturers understood the objectives and were enthusiastic about them. The clear view from the rear door of the OV-10 offered additional advantages for unconventional warfare that I need not go into here.
Now comes the sad part. The development of NIFAC capabilities was approved, but direction of the development was entrusted to a completely new group of people, none of whom had had any contact with the earlier study group. I attended one of their meetings, probably the first, with representatives from the manufacturers of the OV-10. I have seldom been so discouraged. The group seemed completely incapable of understanding the purpose of the project. They had closed minds. All they could think about was putting weapons systems on the OV-10. I heard afterward that they had added so much weight that the aircraft could barely get off the ground to perform its NIFAC mission.
CHANGE OF FOCUS TO EUROPE
After its escalation, the Vietnam War dragged on into the early 1970s. Before it was over, our military thinking was reacting to a major change in NATO policy, which is still, to a surprising degree, unknown to the general public, a fact that I regard as a danger signal. In January 1968 the NATO policy of “flexible response replaced the “trip wire” nuclear strategy. Under the earlier strategy any incursion of Warsaw forces into West Germany would have triggered an immediate full-scale nuclear response. Under the new policy of flexible response, a conventional attack by Warsaw Pact forces would be met by a conventional response until things got out of hand, at which time NATO would use tactical nuclear weapons in a “flexible” manner. This new policy insisted on the concept of “forward defense,” which meant essentially that every inch of West German territory must be defended.
The focus of our military thinking switched to this new problem of high-intensity conventional war in Europe—to the total exclusion of limited war elsewhere. The thinking of the 1960s was forgotten—a pity, since some of it was very good and is still applicable to non-European threats that we may have to face in the future.
As a result of this change of focus I was asked, early in 1972, to study the Soviet capabilities for military operations in and around Europe. I found that, as early as 1953, R. L. Garthoff’s Soviet Military Doctrine had made it evident that U.S. and Soviet views on fundamental military problems were widely different. Eighteen years later, in 1971, the Royal United Services Institute published a : defense study, Soviet Military Power, by Professor John Erickson of the University of Edinburgh. It was a study in depth, based on a large number of Warsaw Pact sources. The reshaping of the Soviet military command between 1965 and 1970 was analyzed and many inferences were drawn from Soviet military training and from the large-scale exercises that had been carried out in the 1960s. Of considerable importance was the “Shield-72” exercise of mid-September 1972, discussed by Erickson in the December 1972 issue of the RUSI Journal. (Remarkably quick reaction.) In this exercise several new trends appeared. It was becoming increasingly evident that Warsaw Pact forces were being structured to conduct a “lightening war” with little capability for protracted conflict. Clearly NATO needed a “lightning response” capability well tuned to what was known about traditional Soviet methods of fighting and about the latest thinking of their military planners. NATO’s “lightning response” needed a defense against enemy ground forces pouring across the borders, but also needed to be prepared to deal with enemy activity in rear areas all over the country.
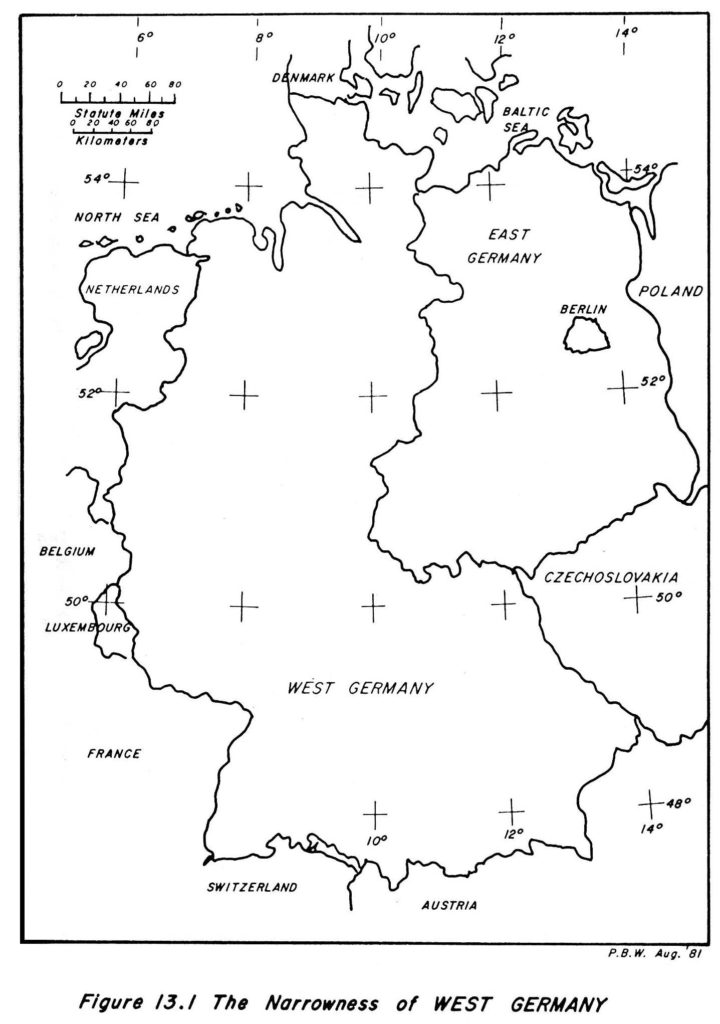
The situation is clarified by Figure 13.1, which shows the narrowness of West Germany. It must be reckoned that, if they choose to do so, Warsaw Pact forces could probably occupy Austria without much difficulty. If this were to happen, no corner of West Germany would be more than 200 miles from them. Indeed, in the extreme north almost the entire extent of the West German coastlines on the North Sea and on the Baltic, together with the border with Denmark, already lies within 100 miles of Warsaw Pact territory.* Soviet thinking envisaged that the planned penetration in a major offensive might reach up to 250 miles. Successive echelons of the attacking force would be organized in depth, so that a new hammer blow could be struck as soon as each echelon lost its momentum. Night-fighting capabilities were already being improved to permit round-the-clock operations. Massive air attacks were to concentrate first on enemy reserves, while many small-scale airborne infiltrations and a number of large-scale airlifts would disrupt the enemy rear. To many military thinkers in the early 1970s it seemed that the response being planned by NATO was utterly inadequate to meet the new situation presented by the Warsaw Pact threat. Yet the doctrine of U.S. Army Field Manual FM 100-5, designed mainly to deal with operations in central Europe, was similar to that stated in French doctrinal manuals of 1940 in that of the two elements, fire and movement, fire was considered to be predominant. The Germans did not think this way—nor do the Soviets.
* These geographic distances explain why U.S. forces stationed in Europe, feeling the proximity of a strong enemy, tend to have views very different from those of the military experts who sit at desks around the United States.
Clearly our military establishment as a whole is still not attempting to acquire a deep understanding of the military concepts of our major enemy. We are still neglecting the vital need to anticipate how the enemy will fight, and this is, to my mind, one of the gravest of all our many danger signals.
From 1972 to 1978 my studies centered more and more on anticipating what the Soviets, with their Warsaw Pact allies, might try to do in the first few hours of a conventional attack against West Germany. In open literature I found a good deal of information on recent trends in Soviet thinking and in their development of offensive capabilities. Today the Soviets are capable of launching a new version of the German blitzkrieg, still based on conventional weapons, but far more devastating than the World War II version. If we were to be caught unprepared, as were the French and British in 1940, our chance of muddling through would be dim, if not nonexistent. Yet today many of our politicians still call only for more defense spending, as if that were the answer. What matters is not the amount spent, but the thinking and planning that directs the spending. The development of increasingly sophisticated weapons systems is easily understood and glamorous. It appeals to our military command, to our armaments industry, to our politicians, and to the general public. But it is by no means the whole answer. In deciding how to spend defense funds, our military has put too much emphasis on spectacular technological achievements, and too little on less glamorous but equally important requirements such as communications—too much on providing computerized capabilities for commanders, and too little on the needs of the combat units that will do the actual fighting. Success on a future battlefield will depend in large measure on how effectively the actions of the many diverse combat elements can be directed and coordinated, particularly in response to a new threat or a new opportunity. This in turn will depend on availability of means of communication that can adapt quickly to new situations and can handle information at the speed called for by ever-advancing technology. As I will show, we have no such tactical communications today—and of what use is any ultra-advanced weapon, or superbly armed combat unit, without a means of communication to bring it into play at the right time and with the right objective? If this planning and development area does not get its proper share of defense money, the vast sums we have spent on weapons and other glamorous items may as well have been poured down the drain.
STRATEGIC COMMUNICATIONS AND GLOBAL THREATS
In 1978 the focus of my studies switched to the achievement of suitable tactical communications for possible future battlefields.
The emphasis, however, was still on situations that might arise in Europe. I will be talking about this later—it brought me back to memories of the Hut 6 experience. First, however, to conclude this discussion of danger signals, I will draw attention to two other sadly neglected areas: strategic communications and global threats.
Our strategic communications capabilities, which include those needed to bring nuclear weapons into play, appear to need urgent attention and adequate defense spending. Even the decision to use low-yield tactical nuclear weapons in Europe, in accordance with NATO’s doctrine of flexible response, would involve the governments of the NATO alliance, and that would require communications of a strategic nature. Awareness of, and response to, critical situations in other parts of the world would depend on adequate communications. Yet today one keeps reading public statements about the unreliability of important strategic communications systems. For example, according to the Wall Street Journal of March 10, 1980, government auditors have concluded that the World Wide Military Command and Control System (WWMCCS), the computerized communication system designed to warn the President of an enemy attack or international crisis, is prone to breakdown. The auditors said the network is unacceptably slow, unreliable, and has failed in at least two recent critical situations. (And this without any enemy intervention.) It has also been reported in the press that, on more than one occasion, we have been dangerously near to launching nuclear weapons, an act that would have started a nuclear war, through communications foulups. What more do we need to convince us that our survival may well depend on having the right Strategic communications capabilities?
In regard to global threats, I have shown that although in the 1960s a lot of thought was given to conflicts that might arise outside Europe, not much was done to prepare for such conflicts, and then in the 1970s the focus moved on to Europe. But events in Angola, Abyssinia, Afghanistan, and Iran, as well as alarming situations nearer home in the Caribbean and Central America, are forcing us to realize that we need new environmental analysis and conceptual thinking about possible threats outside Europe, some of them by no means directly related to the Soviet Union.
We should not, for example, neglect the possibility that, if some Latin American neighbor becomes sufficiently irritated with the United States, its government—or a powerful rebel force making a bid for power—might ask for Soviet military assistance. There is little doubt that, with their tremendous development of merchant marine and airlift capabilities, the Soviets could very quickly transport a substantial military force to an area from which they could then threaten the United States.
Thus global threats are not only very real but also continually changing, and they call for frequent reappraisal. If we fail to anticipate the special communications problems that may be involved in countermeasures, we are likely to find ourselves in trouble. In this context I am reminded of a lecture on crisis management given at MITRE in March 1973 by Dr. Thomas G. Belden, then Chief Historian, Office of U.S. Air Force History. He analyzed the glaring weaknesses in communication that had showed up in the stories of Pearl Harbor and the Pueblo incident. In each case he exposed failures to anticipate and to set up the proper communications procedures ahead of time. He also stressed the vital need in a crisis for rapid establishment of secure conferencing, both vertical and horizontal, among the elements involved—very true of a crisis that might call for a decision on whether or not to use tactical nuclear weapons in Europe. He argued that even the most advanced means of establishing secure voice conferencing were far too slow, which is still true. He urged a return to “conversational teletype,” which would have been perfectly satisfactory for the types of crisis conferencing he had studied. This still makes good sense, but teletype communications are old-fashioned—definitely not glamorous.
Belden also introduced the idea of developing standard message formats to ensure that, in various types of crisis situations, no essential items of information would be omitted. This is an old idea that has been applied to many management problems, but it calls for imaginative thinking and it does not involve glamorous technology.
Belden was absolutely right, I believe, in suggesting simple measures that would greatly improve our response to future crises, large and small. The danger signal is that such ideas have not been implemented. We are no better able to handle a crisis now than we were at the times of Pearl Harbor and the Pueblo incident.
As we have seen, the Germans in World War II were on the whole well served by their communications system. But as I have pointed out, the part of the system with which I was concerned operated reliably only because the controllers of the nets worked continuously to keep them in good order. A communications system whose satisfactory operating condition is not frequently verified by actual tests is liable to fail when it is needed. Indeed, failure to make sure that an important line of communication remained continuously open was one of the main troubles in the Pueblo incident. Taking steps to see that our vital means of communication are kept in working order may be less glamorous than improving the performance of a weapons system, but surely the expenditure needed for this purpose should have high priority in the allocation of defense funds.
14
Military Considerations
THE PEAK AND THE RUT
The nature of our present situation was brought out in a lecture on “Advanced Technology in Modern War” given at the Royal United Services Institute, Whitehall, London, on November 26, 1975, by Mr. John A. Morse, formerly Deputy Assistant Secretary of Defense, Pentagon; International Security Affairs, Europe and NATO. He argued that our main problem at that time was a thinking rut, thirty years deep. Both political and military leaders were stuck in it. Morse said that this rut simply must break up before long, and predicted a revolution in military operational concepts, doctrines, and tactics. If we do break out of the rut, he went on to say, the military technology already available, or likely to be available within five years, offers great promise. This advanced technology can provide better ways to deal with problems we face now, and with those we will face in the future, and it will do so at costs we can afford if we use our assets more effectively and efficiently.
Since 1975 a conceptual debate has been building up, resulting in increasing pressure for change, but the predicted revolution has not yet materialized. In what follows I will be discussing ways in which my personal experience, and what I have learned in the course of my work, may be applicable to today’s problems. My experience in Hut 6 was concerned with communications of the German army and air force. In recent years, too, my study of military communications has been focused on the needs of ground and air forces. I have searched for military case histories, drawn from actual combat, that can help us to prepare for the realities of future battles. I have also been in close touch with one particular development of military communications technology that does indeed offer great promise.
This example of available technology will be discussed in the next chapter. Its potential value will be illustrated by showing how it could have been used to great advantage by the U.S. Air Force in Vietnam. In the present chapter I will present a few historical episodes that can help our military planners to achieve a realistic approach to problems of the future. In particular I will draw attention to events that took place in the African desert during the short period from May 26, 1942, to July 10, 1942. In nearly twenty years of study I have never found an episode in military history that contains so many lessons for the future in the areas in which I have been working. Nor have I found a story of actual war that so clearly mirrors what I believe to be wrong with our current army thinking, at least in the areas discussed in this book.
Let us first go back to the time, in World War II, when the Allies were preparing to invade France. American air offense against targets deep in enemy territory was to be handled by the U.S. Eighth Air Force, based in England. The U.S. Ninth Air Force under General Hoyt Vandenberg was preparing to support the ground forces by attacking targets at the front and in the immediate enemy rear. The planners, in spite of protests from Washington, refused to be governed by earlier doctrinal thinking. They were designing an organization for joint ground/air operations on a scale without historical precedent. Experience in the African desert had shown that cooperating air and ground headquarters must work very closely together. Consequently Ninth Air Force headquarters was so designed that a compact, highly mobile “advance headquarters” could move with the Army Group and handle air operations, while the large “main headquarters” handled administrative matters. Under the Ninth Air Force there were three Tactical Air Commands (TACs) cooperating with the First, Third, and Ninth Armies. Again each TAC headquarters was divided into advance and main sections, so that the former could move with»the associated Army headquarters. Thus XIX Tactical Air Command under General Otto P. Weyland supported Third Army under General Patton. In its first month of operation Weyland’s advance headquarters moved five times to keep up with Patton’s headquarters. For periods of particularly rapid movement a “super-advance” headquarters was used, consisting of Weyland, an operations officer, an intelligence officer, and communications personnel. Similar arrangements applied to the other TACs, and there was also close cooperation with the British Second Tactical Air Force, which was the air partner of the 21st Army Group.
Army-Air cooperation was carried down to corps and division levels by Tactical Air Control Parties, and sometimes right down to the front line by Air Liaison Officers. An ALO could ride with the lead elements of an armored column and be given authority to divert fighter missions headed toward targets of opportunity in the enemy rear to targets in the immediate vicinity of the column. The ability of the overall organization to adapt to an unexpected situation was tested on many occasions. Commanders and their staffs were encouraged to introduce new functions and more efficient operating procedures, and to eliminate functions and sections that had outlived their usefulness. The Allies had come a long way from the rigid, outmoded doctrines with which they had entered the war. They had outdone the Germans with their own ideas of blitzkrieg. Driven by necessity, they had reached a peak in military thinking and accomplishment.
After many months of careful study by officers who were directly involved, a “Condensed Analysis of the Ninth Air Force in the European Theater of Operations,” with many conclusions and recommendations, was published in March 1946, while memories were still fresh. The basic conclusion, as General Vandenberg declared in a foreword, was that flexibility and mobility in thought, policy, and action are essential to success in war. He warned that, if a tactical air war were to be fought in some other part of the world, it would be highly dangerous to assume that the policies and procedures developed in the European theater would be appropriate. Each new environment would call for new thinking.
As far as I can discover, this excellent “condensed analysis,” which recorded the experience of our tactical air forces at the peak of their performance, was almost totally ignored by the peacetime military establishment. If its recommendations had been followed, we would have fared better in Korea and Vietnam. Instead a thinking rut developed in the area of tactical air operations. I imagine that much the same is true in other areas, resulting in the overall situation that Morse perceived.
Morse also pointed out that, in prolonged periods of peace, the development of a thinking rut in a military establishment is perfectly normal. This being so, it is not going to be easy to develop the kind of military thinking that we will need in war. But, until we wake up, the development of new capabilities will continue to be far too slow. There is the grave danger that we may be overrun in our sleep, as were the French and British in 1940, and, in view of the far greater pace at which things move today, our chance of muddling through to a turn of the tide will be far less than theirs.
BATTLE OF FRANCE
Because the realities of war involve so much that is absent from peacetime experience, and because we need to form realistic pictures of what the initial phase of a Soviet blitzkrieg may be like, it seems clear that we will do well to examine the causes of the phenomenal success of the German blitzkrieg in France against an allied force that outnumbered them and had weapons superiority in some areas. Indeed when, around 1970, the focus of our military attention switched to conventional war in Europe, it became important to study World War II. Far from being out of date, that war seems extremely up to date when compared with our peacetime thinking. It was the most recent major European conflict. Its events and patterns can be expected to have at least some similarity to those of future non-nuclear, combat in that part of the world. Hence its firsthand source materials, which are largely unknown to most Americans, should not continue to be neglected. We live in a world very different from that in which the Second World War was fought, yet parts of the story, including the matters I have described related to Hut 6, contain lessons that are still valid. They may be the best lessons we have. It would be foolish to ignore them. Two books in particular that tell us a great deal are Panzer Battles by ‘. W. von Mellenthin, and Panzer Leader by Heinz Guderian.
Guderian, who was one of the principal architects of the German blitzkrieg, led a German panzer drive through the Ardennes. Starting early on May 10, 1940, he reached the river Meuse on the evening, of May 12. A major panzer breakthrough beyond the Meuse was achieved on May 16. The coast of the English Channel was reached on May 20, and by May 21 the Allies had lost all hope of recovery. The distance covered in ten days was a little over 200 miles, an achievement well worth our attention.
Guderian’s detailed story of his drive to the Channel coast is fascinating. Even today it is extremely relevant to our thinking about the possibility of a Soviet blitzkrieg in Germany. It emphasizes the critical importance of quick response to the “initial test”—to a new situation that is suddenly thrust on us. It shows that the Germans could have been stopped in that campaign if the Allies had responded quickly enough with appropriate countermeasures. At the onset, the critical crossing of the Meuse near Sedan was forced by infantry units without waiting for the arrival of artillery. Air attacks substituted for artillery fire, and succeeded in neutralizing the French artillery. This decisive use of air power to support the river crossing had been planned to the last detail by Guderian and Lieutenant General Bruno Loerzer, commanding Air Corps II. The army-air discussions on the matter had taken a month, but on the previous day the plan had been countermanded by General von Kleist, Guderian’s superior commander, in agreement with General Sperrle, Loerzer’s superior commander. Much to the surprise of Guderian, who was watching the long-planned crossing by the 1st Rifle Regiment of his 1st Panzer Division under Lieutenant Colonel Balck (later to become a distinguished panzer general on the Russian front), the air attacks went according to plan, and were extremely effective. General Loerzer had decided that the new orders from higher command had come too late to be implemented!
This was the first of several occasions on which Guderian’s chances of success were nearly ruined by the German higher command, which did not have an intimate knowledge either of the planning of their operational commanders or of the opportunities that were arising on the battlefront. Guderian, however, was on the spot and managed to drive his troops on, taking full advantage of the slowness of his enemy’s response.
A major factor was the dismal failure of the French to keep pace with the German development of military radio communications. This is discussed in “France 1940: Anatomy of Defeat” by Lieutenant Colonel Frank E. Owens, U.S. Army.* After the war General Gamelin (the Allied Commander in Chief) testified that it normally took forty-eight hours for an order issued at his headquarters to be executed at the front. A British liaison officer with the French in Belgium reported that there were no radio communications whatever among the 1st Group of Armies. The French were forced to rely entirely on dispatch riders. Indeed they had no means of communication speedy enough to coordinate their operations against the well-coordinated and fast-moving German armored attack. This held true from the highest headquarters to armored units, where flag signals were the only means available to dispose and maneuver tanks—just as in the U.S. Army before the winter of 1940-41.
* Owens was Deputy Director, ADP Support Division, U.S. Army War College. The tide appeared in Army Magazine, December 1972, and in Signal, December 1973.
Von Mellenthin, author of Panzer Battles, was a staff officer who saw a great deal of the fighting throughout the war. We will do well to look carefully into his analysis of the principal reasons for the success of the German forces in France, Belgium, and the Netherlands in 1940. He says:
Our panzer corps and divisions not only had the advantage of excellent training and communications, but the commanders at every level fully appreciated that panzer troops must be commanded from the front. Thus they were able to take immediate advantage of the rapid changes and opportunities which armored warfare brings. Perhaps I should stress that although we attached the greatest importance to armor, we realized that tanks cannot operate without the close support of motorized infantry and artillery. Our panzer division was a balanced force of all arms—that was a lesson which the British did not learn until well into 1942.
Notice that von Mellenthin, in his analysis of the Battle of France, makes no mention at all of the excellence of Germany’s weapons systems! (Indeed in 1940 the British Matilda tanks were superior to the German tanks.) He ignores weapons to concentrate on others aspects: the importance of a balanced force of all arms, [command from the front (not a part of recent U.S. doctrine, though practiced in U.S. forces in France after the Normandy invasion), and, first and foremost, excellent training and communications.
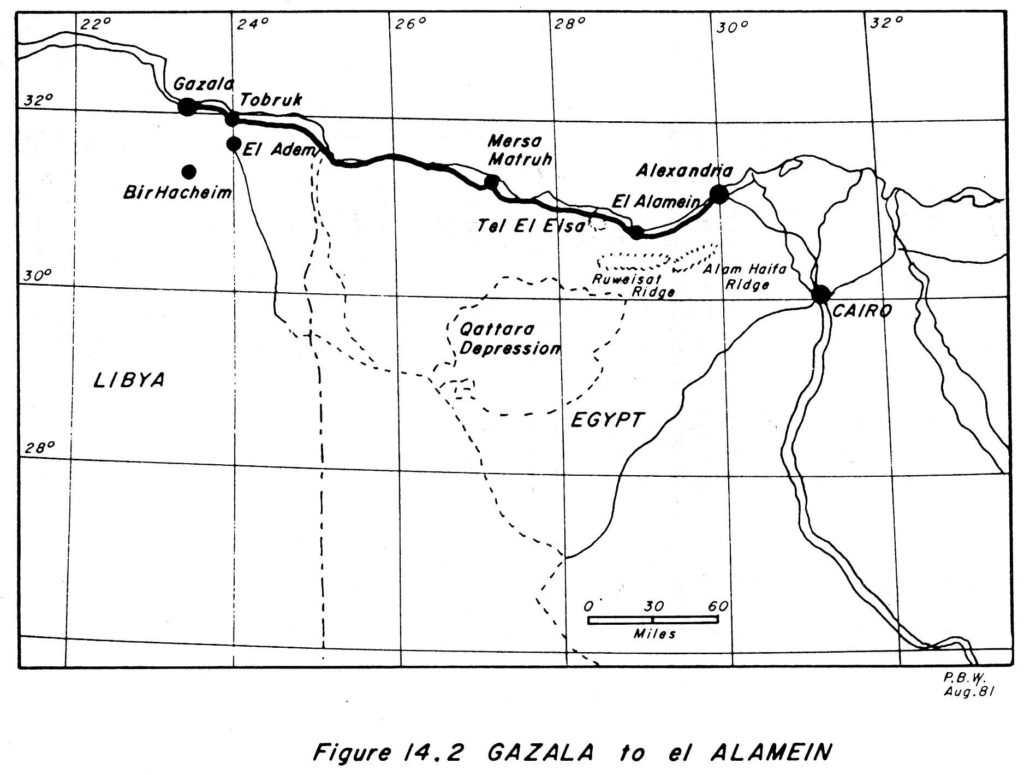
The British learning process, to which von Mellenthin refers, occurred while their Eighth Army was fighting Rommel’s Afrika Corps in the African desert. It occurred before Montgomery’s first defeat of Rommel in the battle of Alam el Haifa at the end of August 1942. I will summarize the story here because it brings out so many of the dangers that must be faced again today. Special attention should be paid to the short period from Rommel’s attack on the Gazala line on May 26, 1942, to Auchinleck’s success in stopping him in the July fighting, which became known as the first battle of El Alamein. (The second battle of El Alamein was Montgomery’s victory of October 1942.)
An account of the desert campaigns, which clearly reveals the learning process, is to be found in Correlli Barnett’s The Desert Generals. The story, however, should also be studied from a different point of view; it brings out the fact that the coordination of overt military actions is not enough. Clandestine activities, too, need to be included in our concept of combined operations. After the turn of the tide in Africa, the Allied victories were greatly facilitated by well-coordinated clandestine activities such as deception, sabotage, and counterespionage. Moreover it is extremely important to recognize that cryptology, intelligence, and secrecy are all weapons of war that need to be coordinated with all the other activities, both military and clandestine. Thus, it is worthwhile to review briefly the seesaw campaigns in the African desert from Rommel’s arrival to his defeat by Auchinleck in July 1942.
THE EARLY PHASES OF THE DESERT CAMPAIGNS
To bring out what was wrong with British thinking and what was done in the middle of a campaign to remedy the situation, it is convenient to divide the story into three parts. First, what led up to the beginning of the Gazala battles. Second, the British defeats of Gazala and Mersa Matruh. Third, the defeat of Rommel at First Alamein. The territory covered by the desert campaigns is illustrated in Figure 14.1. Very roughly we may think of Tunis to Tripoli to Benghazi to Tobruk to Alexandria as being four comparable distances along a narrow coastal strip flanked by inhospitable desert.
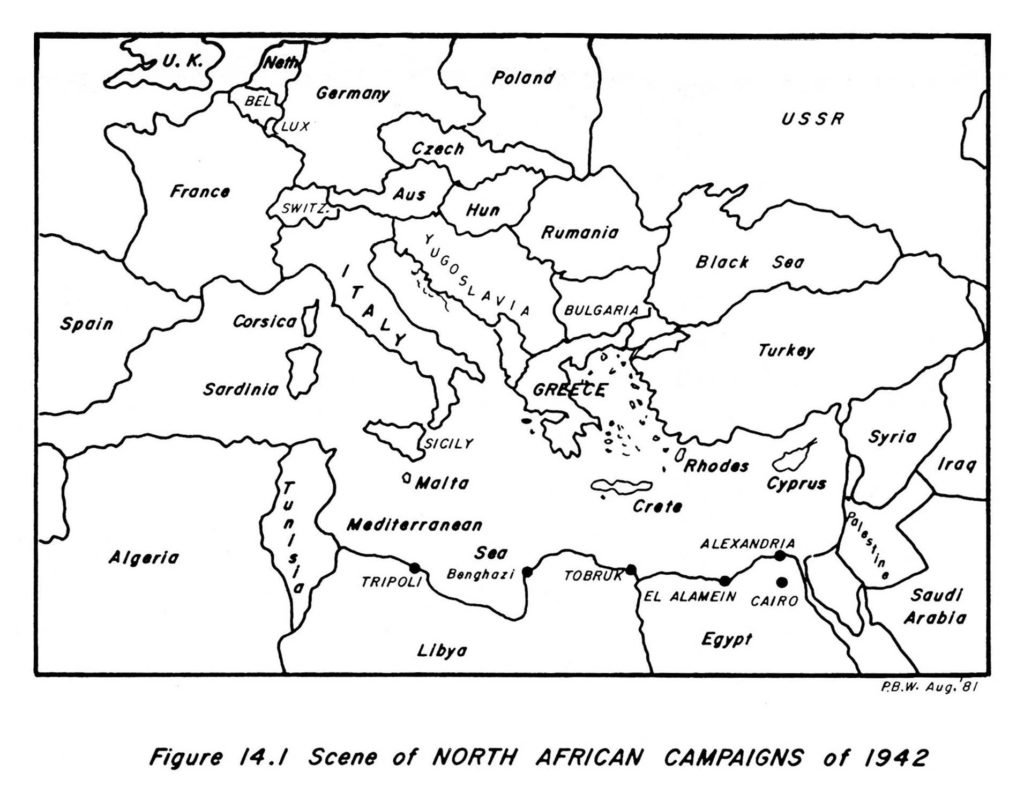
In 1940 the British under Sir Richard O’Connor had won overwhelming victories over the Italians, culminating in the capture of Benghazi in February 1941. Then Rommel came to Africa. In his first offensive, Rommel took Benghazi and besieged Tobruk, a bastion that for the moment held out against all his efforts. At that time Hut 6 was breaking Enigma traffic pretty regularly, and our decodes told the story of the arrival of German forces in Tripoli. They revealed that by May 1941 General Wavell, the British theater commander at the time, was faced with two armored divisions much sooner than he had expected. Winterbotham remarks that it was the accurate knowledge that Wavell and O’Connor received from Ultra of the buildup and strength of the Afrika Korps that enabled the fighting withdrawal of the British and Imperial forces to be carried through without complete disaster. But if the British had a valuable asset in intelligence, the Germans had a big, if not decisive, advantage in communications. British tank radios in Africa had components that could not survive the environment. So long as the British were fighting the Italians it was tank against tank—one on one—and the British were victorious. When the German Afrika Korps came in, the British found themselves up against a force that was well coordinated by good tank radios, and that was quite another matter. This, combined with Rommel’s command from the front, was enough to account for such a severe reverse.
Having brought up the subject of British tank radios, it is a good moment to recall the similar unpreparedness of the Americans. The U.S. Army seems not to have recognized the need for revolution in battlefield communications until it was demonstrated by Hitler’s early successes. Indeed the “remaking” of U.S. Army communications for armored warfare did not start until the winter of 1940/41, at which time the Army had few tanks, none of them with radios. When it got going, however, the “remaking” was rapid. Experiments with cavalry radios were unsuccessful, but the tanks of the U.S. 1st Armored Division were equipped with police FM radios in time for their deployment to Africa in November 1942. By the end of that year a crash program at Bell Labs had produced the SCR 508, which proved superior to the German tank radios. The U.S. communications engineers had also dealt with other problems that were special to tanks—intercommunication inside the tank and the need to shield equipment from ignition noise. Tank crews wore crash helmets for protection; the intercom gear was simply built into the helmets.
A British offensive code-named Crusader started some 50 miles to the southeast of Tobruk, still held by the British, on November 18, 1941. The British tanks had superiority in numbers but were completely unsupported. In a series of cavalry-type charges on the morning of November 2 3 they tried to get at the German tanks, but found them supported by motorized infantry and artillery. They were shot to a standstill by the German antitank weapons. Out of 450 cruiser tanks the British Eighth Army lost at least 300. This disaster, Barnett says, was due to the cumulative and accelerating effects of twenty years of military decadence—the period of peace between World Wars I and II. The Eighth Army commander, General Sir Alan Cunningham, sent an urgent request to the new Commander in Chief in the theater, General Auchinleck, who flew in at once to handle what had become a crisis. Under Auchinleck’s firm guidance the British recovered. He found out, possibly through Hut 6 Ultra, that Rommel’s tanks were running out of supplies. He replaced Cunningham with General Sir Neil Ritchie. On the night of December 7/8, 1941, Rommel began to retire. On Christmas Eve the British were again in Benghazi.
The next phase was another disaster for the British. Between January 21 and February 4, 1942, Rommel drove the Eighth Army all the way back to Gazala, not far short of Tobruk (Figure 14.2). As David Kahn reveals in The Codebreakers, this part of the story started in Rome in August of 1941, when laxity of security precautions allowed an Italian, who had worked for the American Embassy for twenty years or more, to obtain or copy a key that enabled Italian agents to open a safe, remove and photograph the American Black Code and its attendant superencipherment tables, and then replace them unnoticed. This Black Code, so-called for the color of its binding, was used by American military attaches, and possibly even by American ambassadors. One American who used the code book and its superencipherment tables was Colonel Bonner Frank Fellers, the American military attache in Cairo at the time. Once the Black Code and its superencipherment system were compromised, he unwittingly gave Rommel just about the most perfect intelligence any general could wish for by his frequent and meticulous reports to Washington.* Rommel knew the source of the Fellers intelligence and believed it. Ritchie was getting intelligence derived from Ultra but, not knowing the source, did not put very much trust in it. Moreover, Rommel’s radio intelligence company under Captain Alfred Seeboehm was doing pretty well, thanks to poor British radio security.
Although Fellers and Seeboehm must have been of immense help, it is clear that Rommel’s success was due in large measure to the continued British failure to match the German combined arms operations. Rommel, like Guderian in France, was with his forward troops, continually taking advantage of opportunities as they arose. At times the pursuit attained a speed of 15 miles an hour. Ritchie’s communications failed to keep him in touch with what was going on.
In weaponry too, British thought at that time suffered from rigidity and departmentalism. The German 88-mm gun, designed as an antiaircraft weapon, was so dangerous that four of them could stop an armored brigade. The British had a magnificent 3.7-inch antiaircraft gun of even greater penetrative power, but it was not used as an antitank weapon in any of the desert battles. It was intended to shoot at aircraft. The army had been supplied with the two-pounder to shoot at tanks. And that was that!
This is an example of the slow response of the British military authorities to new ideas. The Germans had used the 88-mm antiaircraft gun as an extremely effective weapon against the excellent British Matilda tanks during the Battle of France, as I well remember from German messages decoded by Hut 6 at the time.**
* In his recent book, Hitler’s Spies, Kahn says that the Italians did not give the Black Code to their Axis partner, but that the Germans cracked it analytically and were reading the Fellers messages by the fall of 1941.
** I have been told that the 88-mm was experimentally used for this purpose during the German involvement in the Spanish Civil War.
After his astonishing drive from Benghazi, Rommel needed time to reorganize before his next major offensive. From early February 1942 until May, the two armies rested. The senior British commanders used the lull to digest the lessons of the winter. During Crusader it had been learned that the Germans would not commit themselves to tank-against-tank battle of the kind the British had hoped for. In every phase of a battle they coordinated the action of their antitank guns, field artillery, and infantry with their tank maneuvers. Thus a cavalry-type attack by unsupported British tanks was bound to be disastrous.
But this was by no means the whole lesson that had to be learned, as Auchinleck clearly saw. He set about a complete reorganization of the British armored forces. His changes were intended to make the separate arms of the British service think and work together in the German manner. His efforts would bring success in the First Battle of Alamein, but before then the British were to suffer through the Gazala battles and those around Mersa Matruh, which lay between Gazala and Alamein.
At the beginning of the Gazala battles of May 26 to June 14, 1942, Ritchie’s defensive dispositions behind the minefields that ran from the sea at Gazala to the stronghold of Bir Hacheim still reflected an outmoded pattern of military thought, inappropriate for highly mobile desert warfare. He established a number of independent strongholds or “boxes” full of infantry and guns. His armor was separate. The troops near the sea, including those in Tobruk, were under the 13th Corps commander, General Gott. The troops in the southern area, including a Free French Brigade in Bir Hacheim, were under the 30th Corps commander, Lieutenant-General Norrie. Ritchie’s headquarters was well to the rear.
Rommel was still getting the Fellers reports, which presumably gave him a clear picture of Ritchie’s dispositions. Although his plan to swing around the southern end of the British defense line had been revealed by Hut 6 Ultra, and his movements had been observed by British armored patrols, Rommel was able to surprise and overrun the headquarters of the 7th Armored Division, part of Nome’s 30th Corps. By midmorning on May 27 the division was no longer a coherent fighting force, but neither Norrie nor Ritchie knew of the disaster; with the capture of division headquarters, there was no one to tell them.
When Norrie heard that Rommel was attacking, he ordered the 22nd Armored Brigade to drive southward to support the 4th Armored Brigade, not knowing that the 4th had already been shattered. Before the 22nd could move, Rommel was on them. News of the enemy advance in his rear finally reached General Gott in the northern sector.
The British response that followed was disorganized. Units from here and there came through the dust and heat haze. Heavy Grant tanks and fresh armored brigades joined in. With his ineffective communications, Ritchie’s knowledge was twenty-four hours behind events, and he was unable to control his battle. Yet somehow by nightfall Rommel’s battle, too, was slipping out of control. He was almost out of gasoline and far behind the British defenses. On the second day German armor was scattered all over the place, sitting ducks for want of gasoline, but the British two-pounder antitank gun could not damage them, and rigid doctrine forbade use of the magnificent 3.7-inch antiaircraft guns.
Rommel was in real trouble—wide open to a counterstroke. But Ritchie, sitting remote from the battle, could do nothing effective. He missed a great opportunity, for Rommel, by his personal leadership, was able to withdraw his panzers to the British side of the minefields in the center of the British defense line. He cleared a passage, and so obtained a greatly shortened supply route. Soon he was ready to resume the attack.
This time Rommel could not be held. In spite of a warning from Ultra, a massive British tank attack ran into his prepared defenses, and lost two hundred cruisers and sixty “I” tanks a little to the southwest of the El Adem “box.” His radio intelligence company picked up clear radio signals that enabled him to surprise the El Adem box and clear the way for his advance on Tobruk, which surrendered on June 21, 1942.
After being driven from the Gazala line, Ritchie proposed to retire to Mersa Matruh, inside the Egyptian frontier, where he intended to fight a final battle for Egypt. But Auchinleck had come to the conclusion that Ritchie was certain to be beaten. He decided to take command of the Eighth Army himself. In the few remaining hours he could not alter Ritchie’s dispositions; nor could he eradicate the rigidity and orthodoxy of prewar British military doctrine, or the slow habits that had been a feature of British fighting since the capture of O’Connor eighteen months earlier. He did point out bluntly that the proudly separatist arms of the service were part of the same army, and told his commanders how he wanted them to support each other speedily to deal with German penetrations. He called for close control and coordination of battle groups by divisional commanders who must make their presence felt on the battlefield. But all this could not affect the battle of Mersa Matruh. British formations not actually under attack continued to be the inactive spectators of those that were. Rommel recklessly exposed himself to counterattacks on his flanks, but the counterattacks, though ordered by Auchinleck, did not materialize. Communications were totally inadequate.
Auchinleck had never wanted to fight at Mersa Matruh; before the battle started, he sent Norrie and 30th Corps headquarters back to El Alamein to reorganize, and assigned the defense of Mersa Matruh itself to the 10th Corps under General Holmes.
Some of the conclusions that can be drawn from Correlli Barnett’s detailed account of Gazala and Mersa.Matruh are as follows: British communications were not only slow and unreliable; their use was not properly organized. A corps commander could, and did, withdraw his forces from the battle without the knowledge of a neighboring corps commander. Units were either not instructed or not equipped to listen to radio sources from which they could hear of impending threats. Information was passed up and down chains of command with little or no provision for alternative routing in case of failure of one link in the chain. There was no means by which the 8th Army commander could communicate directly with forward troops if and when he needed to. Moreover, thanks to ingrained habits of thought, it was no easy matter for Auchinleck, the theater commander, to get his troops to fight as a coordinated combined arms force. That he succeeded well enough to win the battle of First Alamein must be regarded as one of the great achievements of military history.
What makes this story so deeply disturbing is that our military thinking of today shows the same types of doctrinal inhibition and compartmentalization that were so disastrous for the British. We badly need to relearn the lesson and to face up to the twin problems of thinking out how our combat troops may be called upon to fight as a coordinated force of all arms, and of providing the necessary communications.
A TURNING POINT
Auchinleck’s victory at El Alamein was a major turning point in many ways. It clearly shows the marked effect on the 8th Army of the new principles and practices that he introduced. It should be noted that, whether or not at his instigation, the Royal Air Force at last abandoned its concentration on distant strategic targets, and took part in the ground battle. It should also be noted that First Alamein was a turning point for Hut 6 Ultra and for clandestine activities in general.
During June 29 and 30, 1942, as the British and Germans raced each other to El Alamein, the RAF poured bombs on the German formations and slowed them down. Auchinleck went out to the coast road to meet his troops and begin to get to know them. The men impressed him and “The Auk” impressed the men. Then he established his headquarters in a place behind the Ruweisat ridge, where he would be within easy reach of his corps commanders. He issued his order of the day: “The enemy is stretching to his limit and thinks we are a broken army. … He hopes to take Egypt by bluff. Show him where he gets off.”
Rommel launched an offensive on the morning of July 1, 1942. Auchinleck had been implementing the operational instructions that he had worked out before Mersa Matruh. He extemporized battle groups that could move and hit. He regrouped all the artillery under his own command so that, for the first time in the desert since O’Connor, his troops were to defend and attack under cover of mass gunfire. He told his army to expect an attack at a very early hour on July 1.
Rommel’s Afrika Korps, in its night approach, had trouble with terrain, and reached its starting points at about six A.M. instead of the planned three A.M. Then, as soon as it was light enough, the RAF contributed an air attack of unprecedented strength. When the panzer army finally got moving, expecting the usual easy morning’s motoring, they immediately ran into heavy fire organized by Auchinleck. As they .struggled forward the fire grew hotter. Another attack in the north around the El Alamein box did no better, the tanks being caught in fire from Auchinleck’s prepared defenses. By midday the northern attack seemed to Rommel to be the more , promising of the two, so he brought in his few reserves and went up in person to drive on the attack. But by late afternoon even Rommel was stuck, as his troops were shelled from all sides by Auchinleck’s newly regrouped artillery. The initiative was beginning to pass from Rommel to Auchinleck.
I want to draw special attention to an action of the 9th Australian division. Auchinleck drew Rommel’s attention away from the coast by a feigned withdrawal to the south of El Alamein. But during the night of July 9/10, massed guns of Auchinleck’s artillery blasted Rommel’s positions west of El Alamein. In the morning the Australians went in and scattered the Italians of the Sabratha Division. The hill of Tel el Eisa was captured, and on this hill was Rommel’s radio intelligence company under Seeboehm. The defeat of the Italian Sabratha Division brought Rommel near disaster. He prevented catastrophe, but only by using German troops he needed for his offensive. Two days later Auchinleck routed the Italian Trieste Division, and again Rommel had to use German troops to avoid complete disaster. By July 17 the First Battle of Alamein was over. Auchinleck had won a historic victory. In the view of Correlli Barnett and many others, it was the military turning point, more significant even than Montgomery’s subsequent British victories at Alam el Haifa and Second Alamein.
From the point of view of Hut 6, First Alamein was indeed the second major turning point of the war. I have found it hard to get the exact chronology from published accounts, but it would appear that in June 1942 the Americans put an end to the Fellers leak by changing the cipher system used for military attache reports. This deprived Rommel of his primary source of intelligence and may account in part for his surprise at the reception Auchinleck had prepared for him at Alamein. Rommel’s loss of the Fellers intelligence may also have helped Auchinleck pull off his surprise attack on the Italian Sabratha Division. Anyway, this attack resulted in the capture on July 10, 1942, of Seeboehm’s radio intelligence outfit, whose location on Tel el Eisa had been discovered by the British Y-Service (radio intelligence). An Australian battalion recovered Seeboehm’s records intact. They revealed a great deal about the help Rommel had received from the Fellers reports and about the success of Seeboehm’s methods.* The British discovered that much of the foxiness of the “Desert Fox” was due to good German radio intelligence in the field and poor British radio security. Widespread reforms in radio security were imposed, and the British formed new companies to monitor the radio security procedures of their own troops.
* There was also information about the abortive Kondor spy mission, the story of which has been told elsewhere.
So long as Rommel was getting superb intelligence from Fellers and from his experienced radio intelligence team, the steady stream of information from Hut 6 Ultra could not be fully effective. After these sources of intelligence had been denied Rommel, Ultra played an increasingly important role. Indeed, from the first battle of Alamein to the expulsion of the Germans from Africa it may be claimed that, with one exception, Ultra played the dominant role in intelligence. Winterbotham has told of the sinking of supply ships, and of the cover stories that concealed the fact that these sinkings resulted from the breaking of Enigma. Ultra helped Montgomery repulse Rommel’s last attack on him, launched soon after the encounter with the Americans at Kasserine, which was the one case in which Ultra did not contribute. American radio security was poor, as British radio security had been not long before, but Rommel’s was good. He ordered complete radio silence before his attack. Eisenhower’s chief of intelligence, Brigadier E. R. Mockler-Ferryman, assumed that there could be no attack without warning from Ultra. Thus the very excellence of the service that was being provided by Hut 6 and Hut 3 contributed on this occasion to a costly defeat.*
* Note however that, as I have pointed out, the German radio nets that would be needed In the battle were almost certainly exercising, even though no Enigma traffic was being pissed. Good radio intelligence could have given warning of the coming attack.
Hut 6 was, of course, a clandestine activity—an important one, but by no means the only one to make a valuable contribution. As we look to the future we should perhaps regard it as no more than a highlight in an overall picture, other parts of which may prove of greater relevance today. In the 1980s our command organizations at home, and our commanders who may have to operate in the field, must worry about a lot more than the cryptographic security of their vital communications. More than ever before they must worry about vulnerability to forms of clandestine attack other than crypt-analysis. If they do not see that such matters as sabotage and spoofing are properly dealt with, who will? And who is going to see that the nation as a whole is not vulnerable to another clandestine weapon—propaganda in its many forms, instigated not only by our enemies but also by our own special interest groups who have little if any concern for national interest?
A very important form of clandestine activity that must be very much in the minds of our future commanders is use of a well-coordinated deception plan that forces the enemy to make errors and achieves surprise, the most precious ingredient in warfare.* Auchinleck’s victory at First Alamein marked a turning point in the British use of deception schemes. This started in a small way as a result of the capture of Rommel’s radio intelligence company, which made him very vulnerable to radio deception. When the new radio intelligence company arrived it had neither the ability nor the experience to distinguish truth from fiction. So the British were able to see to it that Rommel heard only the whispers they wanted him to hear. But radio deception was soon to be coordinated with many other means of conveying false information to the enemy, great care being taken to ensure that all such efforts would confirm and reinforce each other. This form of clandestine activity became a science, employing experts from many fields, including the magician Major Jasper Maskelyne. Who better than a conjuror to draw the enemy’s attention away from what you do not want him to see?
* In the words of Liddell Hart, “Surprise is the supreme virtue of warfare, originality of mind the quality that breeds it.”
The idea was applied in August 1942 and contributed to Rommel’s defeat by Montgomery at Alam el Haifa, when he made his last attempt to break through to Cairo. It was applied on a larger scale in preparation for Montgomery’s victory at Second Alamein. It was applied on a grand scale in preparation for the Allied invasion of Normandy. At the very least these coordinated deception plans considerably reduced the casualties involved in the ultimate achievement of victory. They are fascinating and complex stories, well worth studying for their military implications, but for my purpose I will do no more than mention a few facets that are related to Hut 6 or to communications.
THE GREAT DECEPTION
In Bodyguard of Lies, Cave Brown describes the origins of the coordinated plan of the high commands of America, Britain, and Russia to mislead Hitler about Allied strategy and tactics. The extraordinary success of the plan (code-named Bodyguard) and the magnitude of its contribution to the invasion of Normandy (code-named Neptune) rested on the skillful combination of many clandestine activities. Among these were Hut 6 and Masterman’s XX Committee with its controlled agents. By late 1943 Hut 6 Ultra was providing accurate information about the disposition of Hitler’s forces—intelligence that helped shape the strategy and tactics of the invasion. At the same time Ultra was often able to reveal the German reactions to many of the deception activities, including those of Masterman’s organization, thus making it possible to reinforce success (an old principle in overt combat applied here in a covert manner). Indeed Ultra intelligence was influencing the strategy and tactics of the deception operation.
Bodyguard included many regional plans, of which the one that interests us here was aimed, successfully, at persuading Hitler that the main Allied invasion of France would come through the Pas de Calais. The three dates, June 5, 6, and 7, 1944, on which tides and moonlight conditions would permit Neptune, happened to come in the middle of a period of bad weather. The Allies were able at the last minute to predict acceptable weather on June 6. The Germans believed that an invasion on June 6 was out of the question. In spite of this, however—and this is a point I want to emphasize—the ever-vigilant Luftwaffe radio intelligence service was not satisfied that all was normal. On the morning of June 5 it had detected massive wireless tuning in England—far heavier than anything intercepted before—and that always presaged aerial operations on the following night. During the night of June 5/6 it intercepted broadcasts from American weather intelligence flights over France, which suggested that, contrary to their normal practice, the Americans were about to undertake a nighttime operation.
The Luftwaffe duty officer was suspicious enough to scramble a few night fighters on air patrol. These were observed at 12:34 A.M. by the RAF Y service. It was the first sign of German reaction on D-Day. Luckily, thanks to the deception, the German patrol planes were vectored between Amiens in France and Arnhem in Holland. By that time the vast Neptune fleet had already entered the Bay of the Seine, but there the skies were empty. Allied radio security must have been good. But it had been a near thing. If the Germans had not been led to believe that the invasion would come through the Pas de Calais, the detection of massive tuning of radios might have had serious results. One must take into account all the ways in which an enemy could break down our radio security—not only the most obvious ones.
In the event, initial surprise was almost complete. The German army was not alerted until 2:11 A.M., when it was discovered that British and American paratroopers were landing. The sound of ships’ engines was first heard at 2:35 A.M., by which time all units of the German 7th Army and 84 Corps were being rushed to their positions.
SABOTAGE
In our advanced planning of the communications on which the success of our military actions will depend, we need to pay far more attention than we do to the threat of sabotage. Although the means available to saboteurs today are far more alarming than those of World War II, we can still learn from the Normandy invasion, which provides striking examples of failure of communications due to sabotage at the outset of a campaign. Our military should be heeding those failures in any thinking about defense against a Soviet blitzkrieg.
As the invasion fleet approached the coast, resistance groups throughout France—having been alerted by the BBC—were preparing to execute the guerrilla and sabotage tasks that had been assigned to them. Their first task on D-Day was to disrupt German communications. All over the country, but particularly in the landing area, the lines went dead as “resistants” dug up and spiked trunk cables and pulled down overhead wires. Operators left their switchboards, electrical power circuits fused, and repeater stations exploded.
To give but one example, this sabotage affected Germany’s 21 Panzer Division, which was stationed only a few miles from the area in which the British paratroopers were establishing their positions. The division’s commander was ready to strike, but his standing orders permitted no private enterprise. He had been told that he was to make no move until he had heard from Rommel’s headquarters. As a result of the breakdown of communications and the general confusion among the German high command, the 21 Panzer Division was kept out of the battle for twelve hours.
To coordinate the “maquis” (French resistance) with the invading forces, a large number of three-man special forces teams had undergone long, intensive training clandestine warfare. Each team was Composed of a Frenchman, an American, and a Britisher. Each was to be assigned an area in which it would make contact with, supply, organize, and control a local force of maquisards. About eighty of these three-man teams were deployed by air during Operation Neptune. One cannot help being intrigued by the simplicity of some of the tricks used by the maquisards to sabotage the movements of German armored divisions. They used cyclonite land mines that looked like cow droppings, planting them among actual cow droppings. They held up the line of march by placing upturned soup plates across the roads. At night these looked through a tank’s periscope like the humps of buried land mines. There are many ways to delay a tank!
The successes achieved by the sabotage of German battlefield communications pretty obviously imply problems that might arise immediately in the event of an attack by conventional Warsaw Pact forces on West Germany. Considering that so many carefully trained three-man Allied teams could be deployed by air into German-occupied France before the Normandy landings, we must anticipate, and plan to deal with, considerable infiltration and well-planned attacks on NATO’s communications, surveillance, and command facilities throughout West German territory, probably aided by already implanted agents. (The Russians put great emphasis on infiltration, and are masters of the art.) To me this makes it quite clear that it is dangerous to think only of defense along the front line (forward edge of the battle area, or FEBA, in U.S. military parlance). In West Germany NATO should see to it that there will be no undefended rear.
The failures in communications planning we have discussed had to do with exchanges of information between humans on a battlefield. Today’s problem extends further still: to the communications needs of sophisticated, partly automated weapons systems. Before determining the potential military value of a nuclear missile Installation or a super-high-performance aircraft, it is necessary to think hard about the communication that must precede the launching of the missiles or the vectoring of the aircraft to specified targets. What flow of information from place to place is needed for the decision-making? How must orders be transmitted to the missile sites, to aircraft controllers, and to the pilots? How long will the process take? And how easy would it be for an enemy, by some form of preplanned sabotage including electronic warfare, to cut enough of the essential communications links to prevent the missiles and the aircraft from being used when they are needed?
The Normandy D-Day landings clearly show how vulnerable command communications can be to simple forms of sabotage. Many other World War II incidents bear this out. Peenemünde is a particularly vivid illustration of the use of well-timed communications sabotage coordinated with a deception plan. By piecing together information from several sources, including Hut 6 Ultra, the British learned of the important scientific work on secret weapons at Peenemünde, on the Baltic. They planned a heavy bombing attack, code-named Hydra, for the night of August 17/ 18, 1943.* The Germans were allowed to learn that a heavy raid was coming across the North Sea, but were led to believe that it would be a raid on Berlin. That impression was created by a succession of small raids on Berlin, carried out by high-flying Mosquitoes** repeatedly following a course across the North Sea which took them near Peenemünde before they turned south toward their target. Night after night this maneuver set off air raid sirens at Peenemünde, and after a time the vigilance of the local defense relaxed. On August 17 the 8th U.S. Air Force exhausted the Luftwaffe in the most violent daytime aerial fighting of the war to that date. As the last of the American bombers were returning to England, the main British night attack force took off and crossed the North Sea to the region of Jutland at very low altitude, keeping under the horizon of the German radar screen. Just ahead of the three waves of the main force the usual small party of Mosquitoes set off for Berlin, where they were to drop marker flares, as if laying out the target for a large raid.
* See Cave Brown, Bodyguard of Lies, pp. 364-368.
** Not to be confused with the later Mosquitoes in Korea.
The deception worked. Nearing Peenemünde, the main British force rose to 7,000 feet for the attack, and the first RAF Pathfinders had no difficulty in marking the target with red flares. Called into action by the Mosquito decoys, the Luftwaffe night fighters that might have intervened over Peenemünde were circling over Berlin some 100 miles away. A bit of sabotage in Holland further disabled the enemy’s ability to respond. General Josef Kammhuber, Germany’s leading air defense expert, had his headquarters at Arnhem-Deelen in Holland, and orders to his air divisions were transmitted over a teleprinter cable that fanned out from the Luftwaffe signals center there. Just as the raid on Peenemünde began, Kammhuber’s cable was cut by saboteurs, and he found himself cut off from all means of directing his air defense forces.
Four thousand men were involved in this British raid, which was one of the war’s most decisive air operations. The destruction was so great that Hitler ordered evacuation of all important activity and production from Peenemünde. The RAF did lose forty-one bombers, but the Luftwaffe reported afterward that, but for the deception and the ensuing chaos—aggravated no doubt by the cable cut—it would have shot down two hundred British aircraft on such a brilliantly clear night. Ingenious but simple means had won stunning success against a powerful, well-organized military machine.
PROPAGANDA
A further danger exists, that of allowing our national will to be eroded by subtle propaganda. This is related to the idea of winning without fighting. In The Remaking of Modern Armies, Liddell Hart talks about what he calls the Napoleonic fallacy: that the national object in war can only be gained by decisive battle and by destroying the main mass of the enemy’s armed forces. He quotes Napoleon as saying “There is nothing I desire so much as a great battle.” In contrast the more subtle 18th-century Marshal de Saxe is quoted as saying “I am not in favor of giving battle—I am even convinced that a clever general can wage war all his life without being compelled to do so.”
Obscured in the mass of miscellaneous secret activities described in A Man Called Intrepid are several indications of ruses employed by Hitler as he prepared for the successive steps of his bid to dominate the world. By propaganda and covert activities he aimed to weaken his enemies so that his overt military battles, when they came, would be easily won. Like Marshal de Saxe he realized that many of his objectives could be gained without a fight. A clear and straightforward picture of Hitler’s activities in Britain and the Americas would be valuable today in suggesting areas in which continual future vigilance may be needed.
He found many supporters at all levels of society, some of them mere dupes, others concerned with promoting their own interests. In Britain he must have done pretty well with propaganda that influenced appeasement-minded citizens and politicians. One particularly bright young mathematician, whom I wanted to recruit for Hut 6, was not allowed to join us because he was a member of a pacifist organization that, although it had enrolled many public figures including dignitaries of the church, was known to be under German influence. We should know more about this sort of organization, and about the help Hitler was able to obtain from such individuals as Joseph P. Kennedy, the U.S. Ambassador to England; U.S. Senator Burton K. Wheeler; and John L. Lewis, president of both the United Mine Workers of America and the Congress of Industrial Organizations (CIO). The activities of German and American industries, such as I. E. Farben, International Telephone and Telegraph, and Standard Oil, should be included in the picture. It is said that Joseph Kennedy told his fellow Americans that the British would be defeated. It seems that many industrialists in America were only too happy to believe that Hitler would indeed become master of Europe, and would offer them preferential treatment in a huge market. Senator Wheeler was a supporter of the America First antiwar group, which was inspired by a massive German propaganda effort. He sold a million of his franked envelopes to America First, according to the Stevenson account, and 1,173,000 copies of Axis propaganda, supplied by German consulates and agencies, were mailed at the expense of the American taxpayer by twenty-four members of Congress.
These accusations suggest that a valuable picture has yet to be fully researched and painted. But the story must be told from the point of view of what Hitler was trying to do: We need to look for what others may be trying to do to us now and in the future.
In the late thirties it must have been hard for Americans to believe that Hitler really intended to annex South and North America, though it now seems certain that he did. Today it is still difficult for Americans to believe that the Soviet drive toward world domination can ever lead to a military threat to their own country, though perhaps we are more willing now to believe that we may be endangered by nonmilitary threats, if not by military ones.
Russia has traditionally been a land power, and its past military leaders have been concerned primarily with operations on the continents of Europe and Asia. Since World War II, however, the pattern of Soviet thought has changed. For the first time in history, Russia’s politico-military leaders find their most powerful adversary on a different continent. In planning gradual isolation, encirclement, and general weakening of all their adversaries, they are striving for a balance among activities in many parts of the world. The coordinated effort aims at expanding Soviet influence and military potential in strategically important areas as favorable opportunities arise. On the one hand the Soviets are building up a powerful military machine designed for offensive action and capable of operating globally. On the other hand they may find it possible, by well-coordinated use of various subterfuges, so to weaken their adversaries’ resolve and power to resist that they will be able, in successive stages, to expand their area of domination without having to fight a major war.
On the evidence of history, and particularly the history of World War II, we simply cannot afford to sit back in our comfortable chairs and suppose the attainment of the political objectives of nations to be purely a military matter. It is very definitely not so today; probably it never was. We do face grave military threats, but the nonmilitary threats may well be far more dangerous. Wars, whether hot or cold, will be won or lost by a combination of activities, some of them far removed from any battlefield, and many of them involving some form of communication directed at the minds of men. Any screen of secrecy that prevents our planners ‘from anticipating future nonmilitary threats should be challenged. As for the military threats, we may well conclude that the conduct of war is very largely a matter of communicating true and false information, and of recognizing which is which.
TRAINING
A great many considerations need to be taken into account in the advanced planning of national defense measures and of the communications needed to make them effective. As has been pointed out, the development of increasingly sophisticated weapons systems is easily understood and glamorous. It appeals to our military command, to our armaments industry, to our politicians, and to the general public. But it is by no means the whole answer. Indeed von Mellenthin did not mention weapons in his analysis of the reasons for the quick success of the German blitzkrieg in May 1940.
We have been thinking of two matters that von Mellenthin stressed—a balanced force of all arms and command from the front. But ahead of these he rates the advantage of excellent training and communications, neither of which have the glamour of weaponry. I have a few comments to make about training, but will postpone most of my discussion of communications to the next chapter.
The problem of training personnel to respond effectively to any situation with which they may be faced on a future battlefield is an important facet of advanced planning that is too often neglected. The objective must be to provide latent capabilities at all echelons in all branches of the services. A dictionary meaning of “latent” is “present but not visible or active.” Thus, latent capabilities are those that, though not in use at all times, can always be brought into play when they are needed.*
* Use of the word “latent” in connection with information and capabilities may be unfamiliar to the reader. Indeed I may well have introduced the idea myself in the course of my studies of tactical communications.
In view of the increasing complexity of warfare, a very important latent capability of each operational unit is that of prompt cooperation with other units when a commander at a higher echelon establishes a special task force to meet a new thrust or to exploit a new opportunity. The units of such a task force may not be accustomed to cooperating with one another. They will have dual responsibility—in the chain of command of their specialized activities and within the task force—but once the higher-echelon commander has spelled out the objectives of his special task force, and its internal command structure, the achievement of objectives will depend on direct cooperation among the units involved. These units will suddenly need information from other units with which they would not usually communicate. One of the objectives of a battlefield communications system, therefore, must be to make such
information “latent”—not present all the time but available when needed.
This idea of an interdisciplinary task force created to achieve a specified objective is essentially what Auchinleck had in mind in his establishment of closely coordinated battle groups. In today’s business world it is known as matrix management.
Important tools of training are wargaming and exercises, aimed at preparing personnel at all echelons for the situations with which they may be faced. Guderian tells us that major German operations, such as his vital crossing of the Meuse near Sedan in 1940, were very thoroughly wargamed beforehand. The troops involved were trained and exercised for their roles, and it was found that the actual course of events would be close to the predictions of the wargaming oracle.
Guderian was concerned with the coordination in battle of tanks, self-propelled artillery, antitank weapons, motorized infantry, and air power. But the Soviet concept of blitzkrieg has gone a long way beyond that of Hitler’s Germany, and there are many more combat elements, including those of electronic and chemical warfare, whose activities will need to be coordinated.
Quite recently I have studied a number of thick documents on which the execution of recent field exercises and war games has been based. The preparatory work is so immense and complex that exercises and war games cannot be performed frequently. And even such massive preparation fails to take important factors into account. In a recent major field exercise in West Germany, witnessed by a colleague, there was no attempt at all to simulate enemy jamming—yet even so the exercise ran into a lot of communications trouble arising from line-of-sight problems, poor management, and interference among radio nets.
Training for combat communications should be simple, focused on specific tasks, and accompanied by intensive exercising. A huge communications manual covering a wide range of possible situations would prove useless under combat conditions, for there is no time to find the correct response to an immediate situation in a large manual. The communications men in combat units need instead to be trained and exercised in simple procedures for handling the specific situations they are likely to face.
This idea of simple training aimed at specific tasks and accompanied by repeated exercises could prove very important on a battlefield. Indeed it seems to be a necessary application of the accepted U.S. Army doctrine that a commander is responsible for training his men. But this kind of training is a job, not for the commander at high echelons, but for the junior officer who will be on the spot. For in actual war the nature of a battlefield continually changes. Only those in close touch with combat operations will be able to recognize new tasks, improvise means of handling them, indoctrinate troops accordingly, and see that the new functions are exercised. If this idea is to work, moreover, the junior officers themselves must be well trained and exercised in this aspect of their responsibilities.
Not long ago—I would guess in the early 1970s—the Soviets set aside a whole year as “The Year of the Junior Officer.” Since World War II, the level of intelligence and education in the ranks of their armies had been steadily improving. The year’s primary aim was to indoctrinate junior officers in the task of training their troops to perform their battlefield functions. I do not recollect seeing an account of the results achieved by the Soviets, nor do I know how much attention they paid to communications functions. However, from anecdotes of a communications sergeant I know that the American junior officers of General Patton’s army did not have the latent capability needed to improvise new combat communications procedures and provide the necessary training in the field. I do not know whether the situation is any better today. Yet it seems evident that combined arms operations will depend for their effectiveness on efficient handling of simple communications tasks by all combat units involved. We must identify, therefore, which simple facts about communications should be part of overall indoctrination, training, and exercising at all levels and in all services. And, in so doing, we must pay careful attention to the handling of intelligence and to matters of cryptographic security. We have seen that failure to pay such attention was disastrous for the security of the German Enigma.
THREE MILE ISLAND
I will close this chapter by talking about the spectacular disaster of March 1979 at the Three Mile Island nuclear power plant, because the causes of this disaster are very relevant to the military problems we must face today. If we are to remedy the faults in our overall defense posture, and in particular the glaring weaknesses of our tactical communications, we urgently need to conduct a wide search for applicable ideas, employing expertise from nonmilitary as well as military fields.
For example, as I will show later, we will do well to take advantage of academic studies in management theory and organizational communications, which have had a major impact in business and industry, where nonmilitary wars are being fought all the time. What I want to show now is that we have an extremely valuable source of ideas in the deliberations of the President’s commission appointed to look into the disaster at Three Mile Island. Lectures on the subject by the commission’s chairman, John G. Kemeny, given at Dartmouth College and at MIT, contain a great deal that is directly applicable to our military problems. For instance the study has led Kemeny to believe that the major problems of today are so complex that they can only be solved by interdisciplinary cooperation in planning, in operations, and in keeping a lookout for the winds of change. We can no longer expect, he says, to muddle through if and when we are faced by further technological developments and new threats. We must pay far more attention than we do to “people problems.”
The Three Mile Island disaster, the worst accident in the history of commercial nuclear power generation, occurred on March 28, 1979. Two weeks later President Carter established a twelve-member commission to conduct a comprehensive study and investigation of the accident. The members of the commission represented the greatest possible diversity the White House could create. Each of them had some degree of relevant expertise, but none of them was an expert on all the subjects they had to investigate. Initially they were led to believe that the accident was all the fault of the operators, but they soon discovered that this was not so. To a man, operators and their supervisors testified that they were simply never prepared for anything like the situation they had faced. At that point the commission, which was concentrating on the equipment, began to focus even more on other matters. In the end their major conclusion was that the real problem was not the equipment but the people. They found “people problems” in more different places than they would ever have guessed at the outset. The greatest fault in the equipment was the poor design of the control room, which was the principal interface with the operator. Kemeny states that the design was thirty years out of date. Otherwise the basic-equipment was found to be extremely good.
In accordance with Nuclear Regulatory Commission (NRC) regulations, operators were only required to be trained for an accident in which one thing went wrong. In this accident three things went wrong simultaneously. What happened is of considerable interest.
During routine maintenance, a minor mishap caused a pump to be turned off, which stopped the flow of water into the steam generator.* As a result the nuclear reactor was not being properly cooled; but this was automatically detected, and two safety devices functioned properly. A relief valve at the top of the pressurizer lifted to release pressure, and control rods dropped, causing the nuclear chain reaction to stop. So far, ten seconds after the mishap, things seemed under control. Then three more serious mishaps occurred.
* It will not be necessary for the reader to understand the functions of the steam generator, pressurizer, and other system components.
First, an emergency supply of water was automatically turned on, but failed to reach its destination, the steam generator. After eight minutes of frantic search, an operator discovered that some manually controlled valves that should have been open had been left closed. Second, a light in the control room showed that an electric-signal had been sent to close the relief valve on the pressurizer, even though this valve had in fact stuck open. Had the operators known of this open valve immediately, they could have solved the problem by closing a second valve from the control room. But it was two hours and twenty minutes before the sticking of the valve was discovered, and by that time tens of thousands of gallons of water needed for cooling had been lost.
Even with the valve stuck open, everything would have been brought under control automatically by the main safety system, which came on by itself two minutes after the initial mishap; but a third thing went wrong. The safety system, using two pumps, was capable of injecting a thousand gallons of water a minute, which would have been more than enough. But the operators turned off one of the pumps and cut the other back so that the rate of water injection was reduced to less than one hundred gallons a minute. This turned a minor incident into a major accident.
Why did the operators do this? To find out, the commission studied the selection and training of operators. They found that the operator school taught button-pushing; it did not teach the fundamentals of nuclear power. A key training device was a computer that was supposed to simulate what could happen in the control room, but the commission found that the computer program was incapable of reproducing the conditions that actually occurred. Thus the operators and supervisors were proven correct in claiming that they had not been prepared for what happened.
But they could have been! By searching a mass of documents, the commission learned of an earlier accident, in September 1977, at the Davis-Besse nuclear plant. A somewhat different initial mishap caused the pressure-operated relief valve to open; the reactor operated correctly, and the chain reaction stopped. But the valve did not close and, when the emergency water system came on, the operators turned it off. However, at Davis-Besse it took the operators only twenty minutes, instead of two hours and twenty minutes, to discover that the relief valve was stuck open. When they closed it, there was no longer a need for the emergency water supply that they had turned off. Little harm had been done; but the conditions at Davis-Besse were far less dangerous, in that it was operating at 10 percent power and was a newly fueled plant, requiring less heat to be removed than would otherwise be the case.
Someone investigating the incident for Babcock and Wilcox Company, manufacturers of the steam supply system, was worried that the operators could have turned off the emergency water supply when all the recorded evidence showed that water was disappearing from the system. He found that the operators had not been watching the water pressure in the core. They were looking at the pressurizer, in which the level of water kept rising—from which they deduced, wrongly, that they had too much water in the system.
The investigator went to one of the top nuclear engineers, a Mr. Dunn, who realized what must have happened and wrote a memorandum pointing out that under certain conditions of malfunction the pressurizer can be full, with water escaping from the top, while the core could be almost empty. It was a possibility that had never been considered before. Seriously concerned, Dunn was saying that operators must be warned that in certain circumstances evidence from the pressurizer can be totally misleading. They must be taught to watch the core as well as the pressurizer, and to keep the emergency water pouring in, because, if the Davis-Besse accident had happened at full power, it could have left the core seriously uncovered and resulted in major core damage. This is precisely what happened at Three Mile Island thirteen months after Dunn wrote his memorandum. If his recommendations had been acted on during this period the major disaster need not have occurred.
In spite of Dunn’s efforts, the training division at Babcock and Wilcox was not willing to change existing doctrine without approval from another division that was concerned with the overall system, the other division, however, was busy with other matters. It seems clear from Kemeny’s account that the Babcock and Wilcox division responsible for training did not have the detailed understanding of systems operation that would have enabled them to see the importance of what Dunn had discovered, or, indeed, to develop adequate training in security measures. As a result of delays, caused in >art by a misunderstanding in verbal person-to-person communication between the heads of the two divisions involved, the necessary instructions to operators did not get out until too weeks after the accident at Three Mile Island. Dunn had very nearly succeeded, jut not quite.
Two other chances of avoiding the Three Mile Island disaster were missed through what can be categorized as gross failures in human communication. An inspector, quite low in the hierarchy of he Nuclear Regulatory Commission, became worried about the implications of the Davis-Besse incident in September 1977. He kept going to his superiors, but got nowhere. Finally he went to see two of the five commissioners of the NRC, telling them about the problem. They took him very seriously and called for an investigation. But this was on March 21, 1979—only seven days before Three Mile Island. The third chance was provided by an engineer associated with the Tennessee Valley Authority, which has similar equipment. Purely on theoretical grounds, this engineer became worried about similar possibilities and issued a number of warnings, one of which concerned the kind of problem that caused operator misunderstanding at Davis-Besse and at Three Mile Island. These warnings were sent to the TVA, to Babcock and Wilcox, and to the Nuclear Regulatory Commission, and for all kinds of reasons none of them ever did anything about it. Three failures of human communication at the receiving end!
When the commission studied the part played by the Nuclear Regulatory Commission, they found that there too the section responsible for operator training was very weak. The requirements for licensing a new plant were too lax. But the greatest weakness was found in the arrangements for enforcing the NRC’s rules and regulations. The so-called “inspection” of plants was an inspection of paperwork. The Three Mile Island plant was checked by an NRC inspector a few months before the accident, but he never looked at a single piece of equipment.
The President’s commission looked at the response of the NRC to the accident, and found it utterly confused. There was a lack of communication, and many resulting actions made matters worse. The famous hydrogen bubble was an example. It was well known to experts in the field that, under some conditions of overheating, a large amount of hydrogen could be created. It was also known to scientists, though not apparently to the NRC, that the hydrogen generated at Three Mile Island could not possibly explode. So the NRC, in its ignorance, spread a warning about a possible hydrogen explosion to the press, and thereby created a completely unnecessary scare.
The commission came to the overall conclusion that the NRC was an agency hypnotized by equipment. It had a firm belief that equipment can be made fail-safe, and as a result the NRC totally ignored the human element in nuclear power. All the individual members of the President’s commission promised not to speak until October 30, 1979, when their recommendations were due to be made public. These included a completely new approach to operator training, graduation on fundamentals before on-the-job training, modernization of the control room, more attention to procedures, planning for overall response to emergencies, location of plants in remote areas, insistence that states have emergency plans, and better public education. The commission concluded that it had not found any problem that was not curable or that led to the conclusion that nuclear power is too dangerous to exist as a viable energy source.
Someone, however, gave premature leaks that distorted the press coverage. The public was given a false account of the commission’s deliberations, concentrating upon what kind of moratorium on new construction permits should be enforced. When the report came out, therefore, everyone wanted to know about the moratorium, an issue that had by then been blown totally out of proportion, and the most important recommendations went largely unnoticed. The biggest story, on new construction permits, never got proper media coverage: a unanimous recommendation that neither a construction permit nor an operating license should be issued until three separate requirements are met: first, that new safety requirements, recommended by the commission and others, have been implemented; second, that the applicant meet a much higher qualification for running a nuclear power plant, including having an acceptable operator-training program; and third, that the construction permits and operating licenses be made conditional on review and approval of state and local emergency plans.
Kemeny himself thinks that, if recommendations like those of the commission are implemented during the next few years, nuclear power can be one of the energy alternatives available to humanity. He is equally convinced that there should be a permanent oversight committee watching over what is being done both by a reformed Nuclear Regulatory Commission and by the nuclear industry. This watchdog committee, like the President’s commission, should be composed of diverse members. It should report at least annually to the President and Congress.
In his lecture at MIT, after discussing the work of the commission, John G. Kemeny went on to discuss the changes in American democracy that are needed for survival in an age that is increasingly governed by technology. His ideas on this matter are similar to hose of John A. Morse, who claims that we have reached a point at which technology drives the world. This depressing fact of life in our times has to be taken into account in our advanced planning. Kemeny is telling us that we must not be fooled by the technology salesmen, who exaggerate the capabilities of their products. Two of the principal reasons for the Three Mile Island disaster were a mistaken belief that equipment could be made fail-safe, and dependence on a computer program to simulate trouble that might occur. Both led to poor training of operators. The same symptoms show up in our military thinking, and affect not only the operators of equipment but the command function as well. For the salesmen have been maintaining that their equipment will do all that is needed, and that computers can tell commanders what to do in battle. We can only hope that a major military disaster will not be needed to prove the technology salesmen wrong,
Kemeny also stressed the need for interdisciplinary teams to work on the major problems of today, many of which are far more complex than Three Mile Island. Each member of such a team will have to expand his own field of expertise in order to contribute to the solution of the problem. His colleagues and superiors in his own field cannot have the necessary outside knowledge for all the problems in which a contribution from their expertise may be needed. So teamwork must not be inhibited by directives from the specialized communities that are represented.
These ideas on interdisciplinary cooperation translate readily into military situations. Let us suppose that at some future date a military task force is created in battle to handle some new situation. Achievement of objectives by such a task force will depend on intimate teamwork among units drawn from different specialized activities. Each such unit must acquire a detailed understanding of the current status and intentions of the other units with which it must cooperate. Superiors up the various chains of command cannot possibly keep in close touch with all the details of combat operations. Their contribution must have been made ahead of time by anticipating problems and ensuring that a subordinate, assigned to the task force, will have the necessary capabilities.
These ideas are very reminiscent of Hut 6, where success depended on uninhibited collaboration at the operating level between outside activities—Hut 3, the intercept stations, and the bombe installations—and internal activities—the Watch, the Intercept Control Room, Central Party, the Registration Room, and the Decoding Room. It must be noted, however, that, apart from our initial intercept facilities, we were an entirely new organization created to handle unprecedented wartime problems. Thus we were not inhibited by rigid doctrine developed in peacetime.
Another similarity between the Three Mile Island disaster and the Hut 6 story, this time with the German side, is that, as a result of poor interdisciplinary cooperation, the operators at the nuclear power station were not given an overall understanding of nuclear phenomena, and there was no interdisciplinary committee to keep an eye on what was going on. I have a feeling that the disaster in the security of Germany’s Enigma traffic may have been due to similar failures.
I have cited many of the technical reasons for this disaster under the title “comedy of errors,” and have suggested that, if the Germans had brought in people from other walks of life to attack the security measures developed by their cryptographers, they might have thought of the bombe. But perhaps the underlying cause was failure to achieve interdisciplinary cooperation, first in planning and training and then in the watchdog function. If experts in Enigma system design, in communications, and in military operations had gotten together, disaster might have been avoided. The Enigma system designers could have been given a clearer picture of how their equipment would be used. The officers who used the Enigma, the signals personnel, and the cipher clerks might all have been trained to avoid the errors that contributed to the disaster. An interdisciplinary watchdog committee might well have spotted weaknesses as they arose. This thought supports my contention that, to deal with today’s problems, experts in the many relevant fields of activity—military and clandestine, offensive and defensive—must work together and learn from one another. The problems are too complex for any other approach.
15
Communications for Combat and Command
INTRODUCTION
It is said that, in the 1930s, when Leon Blum was Premier of France, Charles de Gaulle warned him about the risk of military disaster. Blum replied that this was nonsense, since France was spending more on defense than ever before. Yes, said de Gaulle; and it is what you are spending it for that concerns me.
Today the Soviet drive toward world domination poses many types of threat in many parts of the world. The ghastly prospect of nuclear war is on everyone’s mind, but in Europe we and our NATO allies are also threatened by a non-nuclear attack for which the Soviets have made very thorough preparations. Our military, in deciding how to spend defense funds, have put too much emphasis on technological achievement in weapons systems and too little on the people who must maintain and operate the equipment—too much on providing sophisticated capabilities for commanders and too little on the needs of the combat units that will do the actual fighting. Success on a future battlefield will depend in large measure on how effectively the actions of the many diverse combat elements can be directed and coordinated, particularly in response to an unexpected threat or a new opportunity. This in turn will depend on the availability of adaptable means of communication tthat can handle information at the speeds called for by ever-advancing technology.. We have no such communications today— and what use is any ultra-advanced weapon, or superbly armed combat unit, without a means of communication to bring it into play at the right time with the right objective?
After World War II, the planning of battlefield communications gradually deteriorated into little more than methods of applying telephone-system thinking and switchboard technology to provide a rigid structure of point-to-point linkages. This is evidenced by the prevailing emphasis on determining “needlines” in answer to the question “Who will want to talk to whom?” The flexible inter-element connectivity that the Germans provided for their blitzkrieg by using interlocking common-user radio nets could have served as a model for our own future planning, but it was forgotten. Perhaps one should say that it was buried as a result of over-prolonged secrecy imposed on anything to do with Hut 6.
In recent years, however, both in the military and in the non-military spheres, progress has been made in the application of newly available digital technology, such as distributed data processing and data-by-the-packet. One of the most revolutionary battlefield communications systems under development today is at present known as the Joint Tactical Information Distribution System (JTIDS—pronounced Jaytids). It can claim to be a truly remarkable engineering development, taking full advantage of today’s available technology; but it is more than that. It stems from serious attempts to foresee the communications needs of combat forces on potential future battlefields in different parts of the world. No comparable attempts have been made since the 1930s, when Germany was planning the battlefield communications systems needed to support its concept of wide-ranging blitzkrieg.
The development of JTIDS equipment is now supported by the U.S. Army, Navy, and Air Force. Proposed applications differ, but successful demonstrations have already proved that the system can indeed offer revolutionary capabilities. However, the equipment in its present form has been aimed at a few specific applications for which funding was forthcoming. Study of a wider range of applications is now being funded, but the rate of progress needs to be greatly accelerated. Our present means of tactical communication would certainly break down in actual battle. They are totally inadequate to deal with the problems of tomorrow. The only solution in sight lies in the development of ideas that were put forward more than ten years ago. The problems have grown more complex since that time, and will be worse still by the time that new capabilities of tactical communication can become a reality. Consequently a new and intensive round of conceptual study is needed. This must be based on an uninhibited review of military considerations. To be effective it will need contributions from many fields of expertise. And, because time may be running out, our national security calls for prompt action.
RESPONSIBILITIES OF COMMANDERS
In this chapter I will be largely concerned with the inadequacy of our present capabilities for communicating on a battlefield and with the sensational improvements that are offered by the application of available digital technology. I will start with two contrasting attitudes to a commander’s duties in regard to communications.
During World War II, dignitaries visiting Bletchley Park would sometimes talk to us about what was going on in the war. On one such occasion the speaker was talking about a commander’s responsibilities in battle. He asserted that a commander must make his contribution before the battle starts. He must do everything possible to give his subordinate commanders and combat troops the best possible chance of success in advance, for once battle is joined events will pass out of his control. I suppose he wanted to tell us that the Ultra intelligence we were providing was a great help in carrying out this pre-battle function in the African desert. Knowledge of enemy strength, dispositions, and intentions could help the commander foresee the course of events, lay his plans, issue his orders accordingly, and so give his army that “best possible chance.”
Looking back, we can recognize this idea that the commander would lose control during battle as part of the outmoded thinking that characterized British operations in the desert at the time of the Gazala battles. Many years later I was to hear a very different story from my colleague, John Clapper, who had been a U.S. Signals Officer during the war and a member of the staff of the U.S. Army Command and General Staff College at Fort Leavenworth, Kansas, after the war. I will repeat what he said in the form in which I copied it down at the time. Although some of the phrases may be regarded as military jargon, their meaning is clear.
Clapper told me that the need to delegate decision-making responsibility during battle is well recognized in the operations of ground forces. Before battle an army task force commander must have defined his battle objectives and methods to achieve them. He must have issued guidance, orders, directives, and information requirements to all command echelons. He must issue standard operating procedures (SOPs) that clearly state what information is to be acquired, what items are to be included in messages, who is to receive messages of each category, and what the recipients are to do with the information they receive. During battle he must use preplanned tactical reconnaissance and communication to obtain information about the enemy and about his own forces. As necessary, he must redefine his objectives and methods. Again using preplanned communication, he must ensure that new directives and guidance will reach all command echelons accurately and in time. Only by meeting both his preparatory and his battle responsibilities can the task force commander ensure that in the heat of battle the junior commanders at all levels will have the best possible chance of using their local initiative effectively.
Note that in this second assessment the commander does not give up hope for exerting his influence after the battle starts, but that the means by which he does so depend largely on his having thought out ahead of time how he wants information to be acquired and distributed on the battlefield, what he wants each recipient to do with the information he receives, and what means of communication are to be used. A second set of communications procedures is to be preplanned for issuing new instructions during battle.
The second statement very clearly defines an important part of the commander’s responsibilities, and presents a challenge to the designers and users of future battlefield communications systems, which must provide the capabilities that the future commanders will need. Yet this definition, though it may be recognized in operations, is contrary to official U.S. Army doctrine, as set out in the July 1976 edition of Field Manual FM 100-5, which is as follows:
In the division of responsibilities on the battlefield, Generals commanding corps and division concentrate the forces.
Colonels and Lieutenant Colonels of brigades and battalions control and direct the battle.
Captains and their companies, troops and batteries fight the battle.
There is no mention of responsibility for organizing information flow.
A few anecdotes, taken from very different environments, will show how communications problems of commanders have been tackled successfully in the past. I believe they suggest ideas that will be helpful in our advanced planning. I will start with another story from John Clapper, who gave me the definition of a commander’s responsibilities in battle. It shows that a commander and his staff must be able to come up with on-the-spot improvisations suited to the situations in which they find themselves. It also illustrates the importance of careful planning of information flow with due regard to terrain in order to overcome the line-of-sight problems to which most of our communications are subject.
My colleague was signals officer of one of Patton’s divisions during the Battle of the Bulge. His division was to attack the German southern flank through hilly country. His division commander, who appreciated the value of communications more than most, took him along to the planning conference. So, knowing exactly what would be needed from reconnaissance patrols, Clapper studied his contour maps and laid his plans. He told each patrol exactly what they were to discover and report. He told them how to report in very short messages, to reduce the chance that they would be heard by enemy radio intelligence. And he told them where to report from, so that they would be within line-of-sight of one of his carefully placed listening posts. It worked like a charm. The division commander received the information he wanted about enemy dispositions. The radio reports were not picked up by the enemy. Complete surprise was achieved, and the attack was highly successful.
In the hope of obtaining guidance for the future, let us also consider a few examples from the more distant past in which communications were well planned by commanders and attention was paid to terrain. I have spoken of Albert James Myer, the pioneer of U.S. Army signaling and inventor of wig-wag. Although Myer himself fought on the Union side in the American Civil War, and rose to the rank of General, many of his assistants and trainees fought on the Confederate side. One of them, a Lieutenant Alexander, was assigned to General Beauregard as signals officer during the Battle of Bull Run. When a strong Union force under General McDowell had turned Beauregard’s flank and was closing in for a knockout blow, Alexander, well placed on a hill to the rear, saw McDowell’s force as it emerged from cover and signaled Colonel Evans, “Look out for your left, your position is turned.” This short wig-wag signal virtually turned the tide of battle. It reached Bee, Hampton, and Jackson, who promptly maneuvered their forces to aid Evans. Their quickly coordinated efforts stopped McDowell. This was the time when Jackson stood “like a stone wall” until Johnstone, who had also received Alexander’s signal, arrived with fresh troops and the battle was turned into a great Confederate victory. Note that the wig-wag system and a well-organized signals unit made it possible for one vital tactical message to be conveyed very rapidly to five front-line commanders who were thereby enabled to coordinate their actions against a surprise attack.
The American Civil War was fought from 1861 to 1865. Two decades later, on April 12, 1886, General Nelson A. Miles of the U.S. Army was put in command of the Department of Arizona. For many years his predecessor had failed to subjugate the Apache Indians under the leadership of Geronimo. General Myer had drawn Miles’ attention to the heliograph, a recently developed optical signaling method used by the British in India. Its simple principle, familiar even to children today, is that a carefully positioned mirror can reflect sunlight to a chosen point at a considerable distance. If a mirror is positioned in this way, with a drive mechanism to compensate for the movement of the sun, messages can be transmitted in Morse code to the distant point by masking the mirror at intervals, so that the reflected sunlight is transmitted in dots and dashes. The clear dry air of Arizona and New Mexico, combined with the almost continual sunlight, provided ideal conditions for signaling by heliograph. Furthermore, this system would not be vulnerable like telegraph lines to sabotage, at which the Apaches had become skilled.
In short order a network of observation and communications points was established, using carefully selected locations on mountain ranges. Guided by this communications network, the U.S. Army, in spite of the rugged terrain, was able to trail the elusive Apaches. By September 4, 1886, less than five months after General Miles’ assignment to Arizona, Geronimo and the remainder of the Apaches had surrendered.
This success story of a blitzkrieg based on speed of communications contains several interesting features. It was of course concerned with small-scale operations in unusual terrain. But, if we take global threats seriously, we too may find it necessary to conduct small-scale operations in which the nature of the terrain will be an extremely important factor. We also may find that sabotage of [our communications, and other tricks that can be played on us even by an unsophisticated enemy, may be disastrous. We should remember how this theater commander saw that his problem could be ‘solved by new technology particularly well suited to the characteristics of the environment in which he had to operate.
Another example of speedy on-the-spot improvisation to meet the particular situation with which a commander found himself faced is an even earlier form of blitzkrieg based on speed of communications, developed by the French under General Bugeaud in Algeria in the late 1830s. Bugeaud developed “flying columns” of troops that could move rapidly to any part of the country without support from any established strongpoints or lines of communications. As in Arizona, the country was mountainous and the air clear. General Bugeaud hit on the same idea of using signaling stations on the mountain ranges to communicate rapidly with his flying columns wherever they might be. The type of heliograph used by General Miles had not yet been invented (it was developed from a device invented in India by Captain E. E. Begbie in 1873), but General Bugeaud obtained excellent results from semaphore signaling. Again we should remember that we may find it necessary in some small-scale conflict to employ the old concept of flying columns, and [that this will probably call for improvisation of a suitable means of [communication.
One wonders whether General Miles, and perhaps Hitler’s planners too, may have been inspired by study of General Bugeaud’s [combination of flying columns and a countrywide signaling network. We do know for certain that in 1959 another French general took full advantage of this episode of military history. In January of that year General Challe of the French Air Force was appointed Commander in Chief of the French forces in Algiers. He immediately set to work to build a super-mobile force of twenty thousand men. Using Bugeaud’s maps, he installed VHF radio repeaters where the old semaphore stations had been located. By this means all of Algeria north of the Sahara was served by a voice radio net. All military aircraft carried radio repeaters, so that any soldier on the ground with a “walkie-talkie” could talk directly to any command post via the radio net whenever an aircraft was in his vicinity. Thus General Challe was able to coordinate all his mobile ground units and all his air resources quickly and effectively.
The successes of Generals Bugeaud and Challe reinforce the lessons drawn from the story of General Miles. But the General Challe story also contains the important idea that every operational aircraft can very easily be made to act as a communications relay.
EARLY CONCEPTS USING DIGITAL PACKETS
I have noted that a U.S. Air Force “master plan” for an advanced air control capability, completed at MITRE in April 1966, contained a new concept, known as AEGIS, for handling position reports from some 120 friendly aircraft. Each individual aircraft was to determine its position in a common grid by a scheme involving triangulation. The reports were to be in the form of short coded digital messages, now called “packets.” The positions of all subscribing aircraft would be shown on screen displays at the command center and in each aircraft. Using AEGIS ideas and the recent possibility of laser ranging, I contributed an ATAST concept that would enable an airborne forward air controller to report the position of an enemy ground target as well as his own. The target locations could then appear on the screen display of an attacking pilot. These two early conceptual ideas, both exploiting digital packet technology, have been considerably improved and extended. Their feasibility has been demonstrated, and their value is fully recognized by many pilots, but after fifteen years the necessary hardware is still under development.
Later, in 1966, I worked out a concept, aimed at combined arms operations, that involved a high-capacity common-user radio repeater net dedicated to the handling of short formatted operational messages as digital packets. I called these packets Unit Digital Messages (UDMs) in recognition of their close similarity to the Unit Records of punched-card terminology. Information-retrieval technology, already under development, was to enable each subscriber to select just the messages he wanted, while rejecting the mass of messages that he did not want. Each UDM was to contain a set of descriptive codes for this purpose, called the “selection indicator” of the UDM.
The concept of a receiver-oriented UDM system for battlefield use arose from studies of military history that I had undertaken in an attempt to develop an insight into the real nature of combat in the various categories of limited war that I had been analyzing. I had found that the planning of communications, even for a single battle, had often been sadly neglected. Over and over again information available to some combat unit had failed to reach other units to which it would have been of great value. I had found vivid examples of this in the naval battles of Midway and Leyte Gulf, and in many episodes from Korea, a war for which we were singularly ill prepared. Moreover, I had become convinced from talks with experienced signals people that the really important tactical messages on a battlefield need not be long—indeed tend to be short— and that many of them could be reduced to a sequence of coded symbols in standard format, much as items of information are handled in punched-card systems. Such UDMs offered many advantages, among them that message assembly in format would ensure that no necessary item would be omitted; there was little danger that a message would be misinterpreted; and communication between combat elements speaking different languages would be facilitated.
The UDM concept of 1966 led to a more ambitious concept of a general-purpose battlefield communications system that could handle teletype, digital data, digitized voice, and digitized pictures as well as UDMs.
In June 1968 I set out my tentative ideas in a working paper on “cyclic information systems” (CIS). The inverted horseshoe diagram of Figure 15.1 was presented, I believe for the first time, to illustrate the basic principles.* The diagram shows five of many thousands of force elements, or “task units,” that could be subscribers to a net, and the single Net Control Element (NCE). I was concerned with the functions and responsibilities of each task unit as an information source (IS) and as a receiving terminal (RT). The IS boxes in the diagram indicate the equipment needed for message preparation and transmission in the form of digital packets. The RT boxes indicate equipment needed for reception of packets, for applying test criteria to the selection indicator of each packet to determine whether it is wanted or not, and for handling selected messages. All the IS boxes transmit on the same radio frequency (or channel) to a central timing repeater (CTR), which we will assume to be on an aircraft or other high-altitude platform. The CTR retransmits each packet on a broadcast channel using a second frequency. It also puts numbered timing signals on the broadcast receiving channel; these are picked up by all RT boxes. The intervals between the timing signals are the time slots on the receiving channel into which packets must be fitted. Using the received timing signals and an internal clock, the IS box of each subscribing task unit calculates the exact time at which it must transmit a packet on the transmission channel so that it will be repeated in an assigned time slot on the receiving channel.
* Since about 1970 virtually the same diagram has been used repeatedly in descriptions of packet communications systems.
The subscribers shown in the diagram who can communicate directly with the CTR are called first-stage subscribers. Other task units who are prevented by distance or terrain obstacles from communicating directly with the CTR may operate in the net as second-stage subscribers with the assistance of a first-stage subscriber. Their IS and RT boxes need not have all the capabilities of the first stage. There may also be third-stage subscribers, such as forward elements with even simpler equipment, who will obtain access to the net with assistance from second-stage subscribers.
My CIS paper aroused quite a lot of interest, and led to engineering design and partial development of a demonstration system. The demonstration was designed to show how the RT boxes of a number of subscribers could select those that were wanted from among the messages continually flowing on the broadcast receiving channel. Selection criteria were quite complex, but the experimental RT boxes handled them without difficulty. Trouble arose, however, with the magnetic tape equipment that was to simulate the broadcast receiving channel by pouring a prerecorded stream of packets into the RT boxes. It proved quite impossible to obtain reliable performance from the only magnetic tape equipment available to the project, and the demonstration had to be canceled. This was a great blow to all concerned, because they were really excited about the concept, feeling that they had something completely new and very worthwhile to demonstrate.
While others were working on the CIS demonstration, I went on looking into various aspects of the overall problem. To determine what characteristics the system should have, I did a lot more reading of military history and studied the forward-looking writings of military scientists. I looked into the problems of exchanging information between nets with different areas of coverage. And I thought a good deal about how a net could be managed by its net control element in accordance with the overall wishes of the commander in the theater of operations and with the changing needs on the battlefield. By late 1970 I had written a two-hundred-page document setting out my analysis of military considerations, system characteristics called for by these considerations, principles of system operation, and methods of net management. The title was Selective Access to Tactical Information, SATI for short—a more suitable name than “cyclic information systems.”*
* The document, M70-97, prepared under U.S. Air Force contract F19(628)71-C-0365, Project 603C, was approved for public release. A greatly shortened version appeared in the February and March 1971 issues of Signal.
I was due to retire from MITRE at age sixty-five in June 1971, so it was agreed that without delay I should go to Washington to obtain reactions to SATI, and to discover among people and organizations any sign of interest, support, funding, or even development work under contract. Armed with my document, I set off in mid-November 1970 on my first SATI sortie to Washington. There, in three days, I had discussions with five organizations. The last of my ports of call was the Joint Services Office in the Pentagon, where I talked to a colonel who was quick to grasp all the important SATI ideas. He was enthusiastic, felt that I had made a good start with the other people I had seen, and asked for several copies of my document. He intended to arouse interest in other quarters and to have a meeting set up for my next visit.
When I met him in Washington again in January 1971, however, the picture seemed a little less bright. The colonel told me that he had discussed SATI with several people in the Pentagon. He and everyone else felt that my analysis of military considerations was fine and that the resulting SATI concept was interesting. They also felt, however, that my approach to a battlefield information system was dauntingly broad and that, because it rested on a doctrine of command responsibility for organization of information flow, it required a revolution in thinking. In the colonel’s words, the general conclusion was that “they didn’t know what the hell to do about it.” I was told that in the Pentagon of those days the word “command” meant “computer,” while the word “communications” meant “TRI-TAC,” a program then aimed at developing a telephone switchboard that could handle the traffic of all three services. The idea of command responsibility for communications was revolutionary, contrary to doctrine, and therefore unacceptable. And that was that!
DEVELOPMENT OF JTIDs
Much of the UDM, CIS, and SATI thinking on how best to meet the communications requirements of combined arms operations is still valid, but it was aimed at environments that could have been expected in limited wars outside Europe in the 1960s. At that time it was considered that war in Europe would go nuclear at once. By 1970, however, the possibility of conventional warfare in Europe had become the focus of our military thinking. The AEGIS study of 1965 had been followed by a series of projects with different names, one of which had just obtained USAF funding for the development of experimental hardware. This was the beginning of what we now know as JTIDS. The far greater threat from enemy weapons and electronic warfare systems in a European environment led to a new approach to the design of a high-capacity common-user radio net handling digital packets. A valuable relative navigation capability emerged from this new approach. The leaders of this MITRE project studied the overall problem of battlefield communications, but the development of equipment and the important study of what formatted messages will be needed had to be oriented toward a few specific applications.
In the early days of conceptual thinking—the mid-1960s—it was realized that a great deal of positional information could be carried on a high-capacity radio net in the form of various categories of UDMs. For example, the pilot of an aircraft assigned to a ground attack mission would be able to call up a geographical display showing the positional data of special interest to him at each stage of the mission from takeoff to return to base. The data, entered on the net by a variety of sources, would include positions of friendly aircraft, enemy aircraft, targets, friendly antiaircraft defenses, enemy antiaircraft defenses, terrain obstacles, waypoints, friendly airfields, and so on. Such a net, serving a battle zone, would carry a mass of UDMs, but by using selection indicators and the positions contained in the messages; the pilot’s equipment would display only wanted information in a chosen sector of the zone. Fifteen years ago it seemed clear that available technology could provide this capability, and moreover, that the effectiveness of fighter aircraft could thereby be greatly increased.
The first Air Force funding for experimental verification of feasibility came in the fall of 1969. By scrounging existing items of equipment, MITRE personnel produced successful demonstrations in New England. USAF funding for engineering development began in 1972. Demonstrations were given in Europe in 1973 in which aircraft tracks over Albania, picked up by AWACS* aircraft over Italy, were displayed in a command center in West Germany. But this engineering development project was tied to the AWACS program, its purpose being the distribution of information concerning aircraft positions observed by AWACS and ground-based surveillance centers.
* Airborne Warning and Control System
Unfortunately, the AWACs application did not fully utilize the capabilities that JTIDs has to offer. It called for transmissions from one terminal to many terminals, essentially in a broadcast mode. It did not call for the high-capacity many-to-many connectivity that is one of the principal features of JTIDS. For example, if a combined-arms task group has to be formed to achieve some particular objective, it is possible in JTIDS conceptual thinking to arrange for each task unit of the group to receive all messages relevant to group activity from all the other task units. An individual task unit need not know the identities of all the other task units that may need his messages. Provided, that each task unit has been told what information to include in reports, and what selection indicators to use, the information can get to all the places where it is needed.
The possibility of providing a comprehensive display for a fighter pilot was perceived in the conceptual thinking of the mid-1960s, and was a prime objective of the JTIDs team. But the JTIDs equipment for the AWACs program was designed for use on the ground or in a large aircraft. It was not suitable for use in a fighter aircraft.
In early 1973 a cockpit simulator in MITRE was fitted with display equipment to demonstrate types of presentation that would be valuable to a fighter pilot. In 1977 the USAF called on MITRE to write specifications for equipment for use in fighters then under development. In the meantime a contractor working for the U.S. Navy had designed experimental equipment suitable for fighters. In the late 1970s this compact equipment formed the basis of a program aimed at JTIDS pods that could be attached externally to existing fighters. The Army had been developing a position location and navigation system for ground elements in an area of combat, and were studying the applications of JTIDS to Army problems. Up to 1979 progress had been made at a disappointingly slow pace, but in this year the U.S. Army became seriously interested in capabilities offered by JTIDS for more effective coordination of ground and air forces, particularly in the area of air defense. In 1979, however, and again in 1980, the USAF wanted to stop the development of JTIDS terminals for fighter aircraft, thereby threatening other developments aimed at facilitating the coordination of air and surface elements.
Many U.S. Air Force pilots, particularly those with experience of communications foulups in Vietnam, have been enthusiastic about [the type of geographical display that could be provided. This is only one of many military advantages that could be gained by developing a general-purpose battlefield communications system. But problems have changed radically since the early thinking was done.
Although the need to be prepared for a massive blitzkrieg in West Germany may be foremost in our minds, it is very necessary to pay attention also to the many types of military action that may be necessary in other parts of the world—a matter that has been neglected since the 1960s. A study with so many facets calls for contributions from many fields of expertise—in fact, for an interdisciplinary effort. It has taken more than a decade to get from the first USAF funding to where we are now. Can we afford to continue at a snail’s pace?
POTENTIAL VALUE OF JTIDs
From my very brief account of the battle of Gazala it will, I believe, be evident that a high-capacity many-to-many communication system such as JTIDs could have made all the difference to the British 8th Army. If every unit had been able to transmit reports on a single net, available to all other units, Rommel’s moves would have been known everywhere, and the rapid organization of countermeasures would have been greatly facilitated. A study of the more detailed account in The Desert Generals will show much more clearly just what JTIDs could have done. I propose, here, to illustrate the potential value of JTIDs by discussing how it could have helped the U.S. Air Force in Vietnam.
When the Vietnam war escalated, the U.S. Air Force introduced its most sophisticated aircraft and its cumbersome Command and Control (C2) Systems. A few anecdotes will suffice to indicate that, whereas in the south we were just grossly inefficient, in the north we allowed our planes to be shot down unnecessarily. I will show that the situation could have been very different if the digital communications system, JTIDs, now being developed, had been available to the commanders and pilots of those days.
The following stories were told to me by a pilot, Kenneth Kronlund, who flew F-4s in Vietnam—magnificent aircraft with varied capabilities, but largely wasted because of C2 system foulups. Ken Kronlund went to Vietnam as a major, having flown aircraft for the U.S. Air Force since 1952. After his tour of duty in Vietnam, he was assigned, in 1968, to the Electronic Systems Division of the Air Force Systems Command to work on Research and Development Programs related to C2 systems. He found himself involved in the supervision of two MITRE programs, one of which was a forerunner of JTIDs. At this point he-began to think seriously about what had gone wrong in Vietnam and why. He soon became enthusiastic about the thinking in MITRE and elsewhere about what recently available digital communications could do for our C2 systems and for our fighter pilots. As project supervisor, he was able to make a major personal contribution to the present JTIDs program.
Our F-4s usually flew in flights of two or four aircraft. Before each mission the flight leader would be briefed. He would be told the mission identification number, the purpose of the mission, and how the mission was to be executed from takeoff to return to base. Usually the mission would involve coordination with other aircraft and with ground-based elements. The flight leader was told how this was to be achieved. He was given the callsigns and frequencies that he would need.*
* Ken’s talk about callsigns and frequencies takes me right back to my early days in the letchley Park school in September 1939. Many things have changed, but some persist.
The initial briefing for a mission could take one of three standard forms. First, in the case of preplanned missions, the details of which had been worked out in advance, the pilot would get his briefing well ahead of time, and would be able to study the problems he would be likely to encounter. Secondly, there were the “scramble missions” intended to provide quick response to a need or an opportunity. Pilots and aircraft assigned to such missions would wait on the ground for “scramble” orders, calling for immediate takeoff. In this case, the pilot would get his initial instructions, or briefing, by radio in the cockpit of his aircraft. Thirdly, to achieve faster response, aircraft could be held in readiness in the air, on Combat Air Patrol (CAP), in which case, also, they would get their briefing by radio.
As he studied the notes that he had made at the time, Ken Kronlund was disturbed to find that, out of some sixty-five F-4 missions that he had flown, only about five had gone as originally briefed. He had “war stories” to tell about his attacks on ground targets, but he found that not one of his positive combat achievements had been included in an initial mission briefing. They had occurred only because he was redirected or had acted on his own initiative to take advantage of some unexpected opportunity. So, instead of telling “war stories,” Ken found himself telling what he calls his “non-war stories” to illustrate the failings of the established C2 systems and the urgent need for change.
It was not easy to pin down the exact cause of each foulup, but a basic reason for most of them was some form of fragmentation. The C2 system was compartmentalized and lacked the flexibility needed for the on-the-spot improvisation at the combat level—so essential in actual battle. Each mission would involve people in different hierarchies, any one of whom, by failing to perform some function properly and without delay, could prevent the mission from doing anything of value. The lack of a common navigation grid was a form of fragmentation. Furthermore, the available means of communication, which followed the fragmentation of command and control, failed to provide the immediate connectivity so badly needed in battle for the coordination of different types of combat elements who would not normally need to communicate with each other. Communications capabilities tended to provide for one-to-one links between individual elements, and for one-to-many links between a command element and its subordinates. Voice radio nets, each operating on one frequency, could provide few-to-few communications for small groups of elements, but there was no provision for the widespread many-to-many links so essential nowadays to the coordination of diverse combat elements who must work together, sometimes on their own initiative, to deal with newly apparent threats and opportunities.
I will recount a few of Ken Kronlund’s non-war stories, not all of which are related to his own missions, but let us first consider the number of different radio frequencies that the leader of an F-4 flight would have to use, remembering that he could operate effectively on one frequency at a time.*
* Actually an F-4 pilot would have a GIB (Guy in Back) who could be operating on a second frequency, but many of our military planes are single-seaters.
At the start of a mission six different frequencies would be needed to talk to the other pilot(s) of the flight, to the Tactical Unit Operations Center (TUOC) associated with his airfield (which, in Ken’s case, was at Da Nang), to the airfield taxi control, to the tower controlling takeoff, to the center controlling departure from the immediate vicinity of the airfield, and to a radar monitoring his progress on the first stage of his route. All this was commonplace to an experienced pilot; but, if the mission involved coordination with some other element, for example an Airborne Forward Air Controller (AFAC), he would need other assigned frequencies. He might also need to talk to the Direct Air Support Center (DASC) to which the AFAC was assigned, or to the Airborne Battlefield Command and Control Center (ABCCC), if not to other elements of the fragmented C2 system—including, of course, the TUOC to which he himself was subordinate.
The success of his mission might well depend on whether one of these many elements sent him information that he needed when he needed it. And this in turn would depend on whether the element knew his callsign and the radio frequency on which he was operating, for without this information they would not be able to communicate with him. So long as his mission was going as briefed, the elements involved should have known how to contact him. But any diversion to another task would probably cause him to operate on a new frequency, which would not be known to elements needing to make contact with him. Moreover, Ken himself might want to make contact with other fighters looking for targets of opportunity in order to enlist their support in attacking a target that he had discovered. To do this, he would need to know what friendly fighters were in his vicinity, their callsigns, and the frequencies on which they were currently operating.
These problems of having to use different frequencies for different purposes would not have arisen if the potential capabilities of JTIDs had been available. All traffic would have passed on one high-Capacity net, available to all elements, both for transmission and for reception. Messages could have been put on the net by any subscribing element, and other subscribing elements could pick off whatever was important to them. The receiving equipment of each element would automatically examine the selection indicators to determine which digital packets should be accepted. System design should ensure that each subscriber would know when a message in which he should be interested was arriving.
Ken Kronlund would often be briefed to establish contact with an Airborne Forward Air Controller in some remote place, only to find on arrival that the AFAC might have been there at some earlier time, perhaps an hour or two or even a day or two ago, but certainly wasn’t there now. This could have been prevented by JTIDs because the AFAC’s JTIDs terminal would be automatically determining his position in the common grid and reporting it on the common-user net. Both the control center handling Ken’s mission and Ken himself could have known where the AFAC was at all times.
On one occasion he was to provide cover for a defoliation mission in the Khe-Sanh area, involving rendezvous with an AFAC and the aircraft equipped for defoliation—both much slower than him. On arrival at the designated place he found no activity. He contacted every conceivable element in the C2 system (his TUOC, various DASCs, radars, etc.) for information and instructions, without success. He requested a mission over North Vietnam. Finally, running out of gas, he returned to base only to find that the defoliation mission had been diverted to another area, and no one had told him. With JTIDs, Ken would have been able to select from the common-user net all messages related to the mission, including the designation of a new target area and position reports from the other participating aircraft.
The reason for the refusal to assign him a target in North Vietnam is almost unbelievable. Coordination among aircraft over North Vietnam was so bad that no two missions were allowed to be flown in the same general area at the same time for fear that they might attack each other. When he made his request another mission was in progress, so he couldn’t go. Moreover there was no adequate coordination between the Air Force and the Navy, which was also sending planes to North Vietnam, so it was necessary to allocate zones and times.
Again JTIDs could have helped, in that the current position of each friendly aircraft over North Vietnam would have appeared on the cockpit display of every other friendly aircraft in the vicinity.
On one occasion Ken was sent to North Vietnam to attack a mobile command post shown on a reconnaissance photograph, but he noticed that the photograph was a month old. Even JTIDs could not have prevented this type of C2 system foulup. More attention to people problems might have done so.
An AFAC, also, had communications problems. If he was in contact with an army unit under enemy attack and wanted to call for air support, he might be able to get through to the nearest Direct Air Support Center (DASC), which could scramble a fighter mission. Often, however, the AFAC would have to call the Airborne Battlefield Command and Control Center (ABCCC), which would pass his request to the 7th Air Force headquarters, which would relay it to a DASC—a process that could well lead to delay. In any case the AFAC’s request, transmitted in the clear, could be picked up by the attacking enemy, who would know that an air attack was to be expected but could not arrive in less than a certain time— perhaps twenty-five to thirty minutes.
In this case JTIDs could have helped in two ways. First, the AFAC’s request, carried on the common-user net, would have been picked up immediately by a DASC that could scramble aircraft, by any aircraft on CAP that could provide faster response, and by any C2 center whose approval was needed. Second, the JTIDs signals could only be picked up and interpreted by highly sophisticated equipment. In the somewhat peculiar environment of Vietnam, JTIDs, with its ability to make information available anywhere, could have helped in a third problem—that of coordinating air support activities with the South Vietnamese Province Chief in the area of operations.
Another of Ken’s “non-war” stories concerns an attack on a ground target that was to be designated by an AFAC who had spotted it. Ken’s F-4 had an accurate inertial navigation system, which gave him his position in Geo Ref coordinates (a system that does not take the curvature of the earth into account, as does positioning by latitude and longitude, but is nonetheless very satisfactory for use in pretty large areas). Both Ken and the AFAC pilot, however, used the range and azimuth system known as TACAN. When told an AFAC’s position in TACAN coordinates, Ken would be able to rendezvous to within 10 miles, which was good enough to establish radio communications. On this particular occasion the AFAC was in the valley that contained his target. Ken in his F-4 came in at a fairly high altitude, so his communications with the AFAC were not blocked by the hills. At this point, however, because TACAN would be of no use in the valley, the AFAC began to use terrain features as a means of guidance.
He described his valley, in which there was a stream that took a turn to the left, and instructed Ken to follow the turn and look for a target with certain characteristics. Ken dropped into a valley that answered the AFAC’s description, followed the stream’s turn to the left, but could see no target. Finding that he had lost radio contact with the AFAC, he climbed to altitude, made radio contact again, and found that the AFAC was in the next valley, which happened to have a similar stream. A frustrating waste of time, particularly because opportunities of attacking ground targets were apt to be fleeting. Again JTIDs could have helped, if the AFAC in his valley had functioned as a subscriber to the JTIDs net, so that his position would have appeared on Ken’s cockpit display.
Over North Vietnam our Air Force pilots had to contend with enemy surface-to-air missiles (SAMs) and MIG intercept aircraft. Under these circumstances, the lack of communications security could, and did, result in our planes’ being shot down. Our aircraft formations operating over North Vietnam talked in the clear and used fixed callsigns. The callsign indicated the unit, which might be a flight of F-4s or a flight of F-105s. Thus the enemy, by listening to our radio transmissions, could learn a great deal. For example, they might know from callsigns that the aircraft of an incoming flight were F-4s. They would also know whether the F-4s were specialized for air combat or for bombing. In either case they would keep their MIGs out of the way and alert their SAMs. On the other hand they might know that the approaching aircraft were the less dangerous F-105s, in which case they would send in their MIGs, which would have a good chance of downing our planes. Sometimes we would fox the enemy by sending in F-4 flights using the callsigns of F-105 units, in which case MIGs would get shot down. In JTIDs planning, there will be built-in cryptographic security both for aircraft identity and for message content.
Lack of security was by no means the only way in which the inadequacy of our communications systems could cause our planes to be shot down. Lack of connectivity between combat and combat-support units could do it. On one occasion a radar controller north of Da Nang spotted two aircraft near Vinh, in North Vietnam. He could tell that they were friendly, but he did not know who they were. The controller could also see on his radar screen that some enemy MIGs were moving into position to attack. All he could do was to send a repeated message on the frequency of the “guard channel,” monitored by all aircraft, saying “You two aircraft flying near Vinh are threatened by MIGs.” But sending such a message without giving the callsign of the intended recipient was comparable to using a hospital paging system to call an urgently needed doctor to the emergency- ward without giving the doctor’s name. The two friendly aircraft were interceptors, flying F-106s, and looking for targets of opportunity. The lead pilot, after some delay, did realize that the radar controller was trying to talk to him, but at that moment his companion was shot down. What went wrong was not simply that the warning message did not get through. The lead pilot of the pair of interceptors heard the message, but did not realize in time that it was addressed to him. If he had heard his callsign, he would have taken notice, but this piece of information, which must have been available elsewhere, had not been made known to the radar controller covering the area in which the interceptors were flying. If JTIDs had been available, the radar controller would have entered the positions of the MIGs on the common user net, and they would have appeared immediately as hostiles on the cockpit display of the two friendly aircraft.
Over North Vietnam our pilots developed methods of knowing the positions of enemy SAMs and dodging them. But in that environment there were not all that many SAM sites. In the event of a Warsaw Pact attack in Europe, the situation would be far worse. It would be a great help to our pilots if all known locations of enemy air defenses could be put on the net so that those of concern to each pilot would appear on his display. In JTIDs thinking, a pilot will be able to vary the coverage of his display, so that he can survey the hazards in the target area as well as along possible routes of approach and departure. If our SAMs are also subscribers to JTIDs, any of our aircraft in their areas of coverage will appear on their displays as friendlies and the chance of fratricide will be considerably reduced. In general, the many-to-many features of JTIDs connectivity could be of immense importance. Information of potential value to pilots would be transmitted on the net by many different elements, including, for example, the weather service, and would be immediately available to all. Each pilot on mission would be able to obtain selective access to what he needs, without being bothered with information he does not need. Studies have shown that widespread use of JTIDs would result in a spectacular improvement in the effectiveness of our fighter aircraft and in their chance of survival in a high-intensity environment. As I have indicated, the U.S. Army is very interested in JTIDs not only for its own use, but also as a means of achieving more effective coordination of ground and air forces in combined arms operations. In view of all this, it is hard to understand why progress has been, and still is, so slow.
16
Secrecy, Security, and Survival
SECRECY AND INTELLIGENCE
In the story of Hut 6 we see many examples of the need for and misuse of secrecy. The security of German Enigma traffic was broken down by Hut 6, which enabled Hut 3 to produce valuable intelligence. But it was important to maintain secrecy about the source of that Ultra intelligence, and this secrecy often had an adverse effect on the survival of Allied forces. A striking case in point is the Germans’ success in taking Crete by airborne assault in May 1941 in spite of the fact that Ultra had revealed every detail of their plans. An inquiry showed that the island need not have been lost if the defending commanders had paid attention to what they were being told. Not knowing the source, however, they had been discounting Ultra messages. Was this a case of excessive secrecy? As we have seen, similar questions arose in connection with the desert battles. On many occasions the Eighth Army suffered serious losses because its commander, not knowing the source of Ultra intelligence, did not accept what he was told about Rommel’s intentions. Yet, as far as I know, there has been no study in depth of the organization and methodology developed for the handling and use of Hut 6 decodes and Ultra intelligence.
At the beginning of World War II, I doubt anyone had the faintest idea of the volume and variety of messages that would be decoded by Hut 6. Existing cryptanalytic and intelligence handling capabilities were quite inadequate. New methodology, new organizations, new interrelationships, and new rules of communications had to be developed. The very newness of the problem resulted in utilization of very able people from different walks of life whose thinking was not inhibited by outmoded doctrine. But one cannot believe that everything was done perfectly. Surely it would be extremely valuable if an interdisciplinary group, similar to the President’s commission on Three Mile Island, could report on what was done well, what could have been done better, and what recommendations for the future can be deduced. And I can see no reason at all for continued secrecy about the handling of Ultra in World War II, though there may be a real need for secrecy about recommendations for our future handling of intelligence problems.
I would guess that an investigation would give very good marks to the methodology developed in Hut 3 for extracting the maximum amount of intelligence from even the smallest details of Enigma decodes studied over a long period. But I suspect that a commission would discover many faults in using this intelligence that could help us in advanced planning. For example, during the Battle of Britain I heard of an RAF duty officer who expressed puzzlement about some chap who phoned him most evenings to say where German air attacks were coming. He never did anything about it, because he didn’t know who the chap was. But the extraordinary thing, he said, was that this “chap” was always right. It was in fact Ultra intelligence. Evidently no one had thought of telling the duty officer that he could trust, and act on, those reports.
Of course, Hut 6 Ultra, though an important contributor to World War II intelligence, was only part of a total picture of which I know very little. Yet, from what I do know, I am convinced that careful study of the obstacles to, and errors in, the use of intelligence in World War II could be of immense importance in our planning for the future.
ADAPTABILITY IN BATTLE
It is evident that many considerations must be taken into account in the advanced planning of the communications capabilities on which the effectiveness of our national defense measures will depend. Let me mention a few considerations that are particularly relevant to our plans for achieving communications security on the battlefield without imposing regulations that will adversely affect the fighting ability of our combat troops.
On a battlefield we need to find means of providing survivable and secure communications for two distinct purposes—for communications up and down the chains of command of the many specialized branches of the services, and also for direct communications among the elements assigned to a combat task force with designated objectives. Attention has been focused far too much on the former purpose, far too little on the latter. The crying need for quick adaptability of both types of communication has been largely ignored. The outmoded communications systems that are still in use today would give our forces little chance against the fast and furious blitzkrieg for which the Soviets have been planning, training, and exercising. Yet our military doctrine takes little account of this. Our main multi-channel system of tactical communications cannot be set up or modified until a time-consuming “needline” analysis has been carried out.* When a subscriber or relay moves, it cannot operate in the system. Even our forward area radio nets, which offer good connectivity for a limited number of subscribers, are regarded as primarily a means of passing messages up and down the many chains of command, not of providing the immediate internal communications needed for cooperation among the diverse elements of a task force assigned to deal with a critical situation.
* The design of a commercial telephone network that is to serve a group of customers is based on an analysis of who will want to talk to whom—in other words, what lines of communication will be needed? For each such “needline” the expected traffic load and urgency will be considered. Unfortunately this commercially oriented thinking has been applied to tactical military communications.
Even in planning for the survivability and security of chain-of-command communications, no account is taken of the fact that, as a result of enemy action, it may become necessary to change our command structure in a hurry. This is illustrated by the Battle of the Bulge, when the German penetration split the American forces in two. It became imperative that two American Armies, the First and the Ninth, be temporarily shifted to the operational control of the British 21st Army Group. At the same time two American Tactical Air Commands, IX and XXIX TACs, operating to the north of the German penetration, had their direct lines of communication to U.S. Ninth Air Force cut or compromised; these TACs were temporarily transferred to the operational control of the British Second TAF, which was the air partner of the 21st Army Group. A Soviet penetration against today’s NATO forces would almost certainly have a similar effect, making it necessary to change the structure of the chain-of-command communications and the associated security procedures.
To see the need for adaptability of lateral communications among advanced combat elements, let us consider what would happen if the Soviets were to choose, as the main line of a major thrust, the boundary between zones assigned to two allied corps. On either side of this boundary there will be divisions, brigades, battalions, companies, platoons, and squads belonging to the two corps, together with artillery and other elements. At all levels there will be a sudden need for close cooperation between elements of the two corps on either side of the boundary. The necessary coordination of combat elements cannot possibly be provided by chain-of-command communications traveling up one side of the boundary, across from corps to corps, and then down the other side. It will be essential to create a special task force composed of elements from both corps, and to provide direct communications among the diverse elements involved, including Air Force units. There will be no time to fuss with needlines. The necessary communications capabilities and security measures must be latent—not in use all the time, but available at very short notice when needed.
The danger of our insistence on an analysis of needlines is illustrated by an anecdote from the Battle of France. Guderian, in his personal account, makes it clear that he took advantage of his studies of French doctrinal rigidity:
We did not imagine that General Frere would advance against us as long as we kept on moving ourselves. According to the basic French formula, he would wait until he had exact information about his enemy’s position before doing anything. So we had to keep him guessing. This could best be done by continuing to push on.
Guderian did indeed push on, and General Frere made no effective countermove. Let us imagine a Soviet version of Guderian. He would know the basic American formula that a needline analysis for a static situation would have to be completed before the U.S. Army could put its mainline direct-dialing telephone system in operation. All the Soviet Guderian would need to do would be to keep the situation fluid.
Indeed, our peacetime thinking on tactical communications has tended to ignore the fundamental objectives of rapid adaptability to unforeseen situations. And this, I am afraid, has been true of our thinking on the cryptographic protection of our battlefield communications.
CRYPTOLOGY HAS GONE PUBLIC
Advanced planning of military communications and associated security measures in the 1980s can hardly fail to be affected by the remarkable developments that have occurred in the nonmilitary sphere. These developments have occurred in three areas: organizational communications, common-user digital networks, and cryptology. In the 1950s and 1960s a rapidly growing number of professionals specializing in organizational communications appeared in several colleges, universities, businesses, industries, and other groups throughout the United States. A spate of attempts to develop a theory of organization had led to awareness of the importance of human communication within organizations. As early as 1938 the Harvard University Press published the now classic Lowell Institute Lectures by one of the greatest organizers of his day, Chester I. Barnard, who declared that “the first function of the executive is to develop and maintain a system of communication.”* This dictum was accepted by the professionals, who analyzed the many difficulties that arise in human communication and tried to devise means of increasing the efficiency of organizations by improving their internal communications. It was some time before the new ideas caught on, but by 1970 a number of academic institutions were offering degrees in organizational communication, and the students who had these degrees were in great demand in business and industry. Since then the number of degree courses offered in management theory and organizational communications, based in part on possibilities offered by new digital technology, has greatly increased, as has the demand for people who hold these degrees.
* The lectures were published under the title The Functions of the Executive. The quotation is from page 226. Note the contrast between Barnard’s dictum of 1938 and the Pentagon dictum of 1970 that the idea of command responsibility for communications was revolutionary, contrary to doctrine, and therefore unacceptable.
Many of the ideas that have arisen in recent studies of management and communication in business and industry apply to military force coordination as well. An important set of ideas concerns the characteristic orientation of different types of organization toward power, role, task, or person. During peacetime the military organization as a whole tends to be role-oriented, aspiring to be as rational and orderly as possible. There is strong emphasis on hierarchy and status. Procedures involved in instituting change are cumbersome, and there is sometimes a tendency to place procedural correctness before task effectiveness. Nonmilitary examples of such role-oriented organizations include many banks, insurance companies, public utilities, and social service organizations. In wartime, by contrast, the military organization in a theater of operations must become task-oriented in a hurry. In a task-oriented business organization, structure, functions, and activities are evaluated in terms of contribution to business objectives, and nothing is permitted to get in the way of doing the job. Structure is shaped and changed to meet the requirements of task or function, and the response to change is rapid and flexible. Businesses sometimes form “task groups” to cope with specific problems, transferring individuals from several specialized branches or departments to work as a team until the task is achieved and the personnel return to their specialized activities.
The year 1970 seems also to have marked a turning point in nonmilitary interest in common-user networks employing advanced digital communications technology. In the previous year, under the sponsorship of the U.S. Defense Advanced Research Projects Agency, a communications network named ARPANET was designed to employ packet switching as a means of linking a wide variety of digital computer capabilities scattered around the United States and extending to Hawaii, Norway, and England. In 1970 the ALOHA system, implemented at the University of Hawaii, broke new ground by introducing the idea of “contention.” Outlying computer terminals transmitted to a central computer via a common 2,400-bits-per-second radio channel. There was a separate return channel from the central computer. Each terminal would transmit a packet on the inbound channel whenever it had data available, and would wait for acknowledgment. from the computer. If two or more terminals happened to transmit packets whose arrival at the computer overlapped, the collision would be detected by the computer and no acknowledgments would be sent. Each of the transmitting terminals would then try again after a certain time interval, made random to avoid repeated collisions.
This procedure was a lot simpler than the time-slot assignments I had envisioned in my 1968 paper on cyclic information systems for military use. But ALOHA’s use of contention is only practical when the packet transmissions from each terminal are infrequent or “bursty”—that is, occurring in bursts interspersed by periods of inactivity. The original ALOHA was wasteful, but other contention schemes were soon suggested to obtain higher efficiency by reducing the time during which the circuit was put out of action by collision.
During the 1970s, interest in common-user packet networks boomed. In May 1979 a symposium on local area communications networks, cosponsored by the National Bureau of Standards and the MITRE Corporation, was held in Boston. A wide range of applications, operating systems, developmental programs, available technologies, and leading-edge research projects was discussed. That symposium was followed by a flood of conferences on packet-communications networks and related matters. It had become one of the hottest areas of research and development. Hopefully this is a sign that an upsurge of serious interest in using packet technology for military communications is approaching, if not already here.
Several speakers at the Boston symposium agreed that it is no longer advisable to rely on “users” of equipment to state their future requirements, since they do not know what could be done for them by new technology that is just around the corner. They tend to ask for improvements in the capabilities they already have, rather than for revolutionary capabilities that they might have. On the other hand the “suppliers”—scientists, engineers, and manufacturers who can make new technology available—tend to be motivated by achievement of spectacular advances in their fields of specialization, and are likely to be only partially aware of the problems to which their achievements might be applied—in the military case, by commanders and combat elements in the heat of battle. Thus there has been a growing need for contributions from the middle ground, where generalists and applications engineers, working in well-balanced teams, strive to maintain a broad view of the problem areas and the technological possibilities. Since new capabilities create new problems, however, it is only too easy for these teams of intermediaries to lose their grasp of the overall situation if they fail to review all its aspects at reasonably short intervals. To sum up, the “top-down” approach to planning and direction of research and development (user states his requirements) does not work any more. Nor does the “bottom-up” approach (industry develops advanced equipment). The approach must work from the middle outward.
Even before the 1970s, digital data communications technology was increasingly being applied on a common-user basis, and a need to guarantee privacy for individual users was becoming apparent. Before the late 1960s almost the only use of encryption was for national security purposes. Since then the revolution in communications technology has been rapid. But at the same time new electronic technology has been making it possible, and more and more inexpensive, to intercept common-user digital data and voice transmissions, particularly those passed on microwave links. Thus individual users have come to need cryptographic means of protecting their traffic from people who could misuse or interfere with it, including commercial competitors and criminals. Suddenly the need for cryptographic technology has burst its old boundaries. The rapid development of widespread public interest in the entire field is evidenced by the establishment in 1977 of Cryptologia, a new quarterly journal devoted to all aspects of cryptology. Indeed by that time cryptology had gone public.
In 1972, in response to the expanding need for cryptography, the National Bureau of Standards started development of a means of encryption that could be adopted as a standard and manufactured in sufficient quantities to carry an acceptably low price tag. The result was what is now called the “Data Encryption Standard” (DES). I happen to dislike the block-encryption philosophy that underlies the DES—but that is irrelevant so long as the system will do the job for which it was designed.
In 1975 a most remarkable breakthrough in cryptography was achieved by two electrical engineers at Stanford University, Martin E. Hellman and Whitfield Diffie.* They introduced the idea of a system in which encoding and decoding are performed with different keys—one public and the other private. This is completely different from the system characteristics on which the World War II achievements of Hut 6 were based, and makes it clear that we are living in a completely different cryptological age. However, in the first account I read of the Hellman-Diffie ideas I found this statement: “In principle these new ciphers can be broken, but only by computer programs that run for millions of years.” This assurance implies that cryptanalysis would have to depend on computers that can only examine one possibility at a time. I am uneasy because I suspect that this might conceivably not be the case.
* The Hellman-Diffie ideas triggered great interest. Important contributions were soon made by Ronald L. Rivest, Associate Professor of Computer Science at MIT, and others.
I believe the cryptographers of today would do well to study why our World War II bombes were so effective. The German cryptographic experts may have reckoned that their vast numbers of stecker combinations would have to be examined one by one. In actual fact, as I have shown, the stecker combinations were virtually useless. An electromechanical machine that had been tailored to the problem was able to examine all two hundred trillion stecker possibilities in around one millisecond. Admittedly I have not studied the new cryptographic principles, and I have no reason for supposing that some newcomer to the game might be lucky enough to hit on a method of attack that would avoid the necessity of trying the possibilities one by one. But it seems worth pointing out that the bombe’s function was to examine each of around one million possible combinations of wheel order and initial wheel settings. For each such combination it could throw out those for which a solution of the stecker problem was impossible. This left only a reasonable number of combinations requiring cryptanalytical investigation. Remember also that our original method of breaking, the stacking of the Jeffreys sheets, made it possible to examine 26 X 26 or 676 possibilities simultaneously, and without bothering about the stecker combinations.
One of the new-style cryptanalysts showed me an article in the New York Times of November 18, 1979, reporting a “Mathematic Problem-Solving Discovery” by an obscure Soviet mathematician. I doubt whether this particular discovery is relevant to the new methods of cryptography, but my overall uneasiness is somewhat confirmed by this statement:
The Russian discovery offers a way by which the number of steps in a solution can be dramatically reduced. It also offers the mathematician a way of learning quickly whether a problem has a solution or not, without having to complete the entire immense computation that may be required.
SECURITY PROCEDURES
If the problems of cryptanalysis have “gone public,” so have those of communications security, and indeed of security in general. In the industrial sector one has to worry about what competitors and criminals may be able to do. In the military sector one has to worry about clandestine capabilities as well as those of an enemy’s regular armed forces. The governmental sector, too, has problems of communications security, including preventing leaks to the media that are deemed damaging to the national interest.
In the 1970s, and particularly in the second half of the decade, there was a revolution in the technology of communication, and in the recognition of what communication is all about. But what we have seen so far is only the tip of the iceberg. We must expect major developments in the 1980s, and they are sure to introduce new security problems. The new problems must be foreseen and faced. This is no time to perpetuate outmoded doctrine—no time to give dictatorial powers to any one community. It is a time to bring together innovative thinking from many fields of expertise.
The present phase of JTIDS equipment development is aimed at the relatively simple military problems for the solution of which funding could be obtained. Cryptographic measures have been designed accordingly. Far more flexible capabilities will be needed, however, when systems in the JTIDS category are applied to the overall requirements of combined arms operations in the 1980s and 1990s—by which time technology will have taken several leaps forward. Patching up deficiencies in cryptographic systems as the problems grow more complex is fundamentally unsound. The objective should be to plan now for the communications systems of the future, and to provide maximum flexibility for unpredictable twists in the security problems.
In my own experience, one-of the more worrying aspects of the present security arrangements is that far too much detailed information about the design and proposed methods of use of JTIDS equipment has been published, or described in open briefings that could have been recorded. It should have been made known long ago that Hut 6 Ultra would never have gotten off the ground if we had not learned from the Poles, in the nick of time, the details both of the German military version of the commercial Enigma machine, and of the operating procedures that were in use. The Germans tried to protect their secrets. Why give ours away?
Moreover, it has become more and more evident that the most difficult problems in security are not purely cryptographic. We must not forget the probability of sabotage attempts on a global scale. The cryptographic protection of the JTIDS system, and of its more widely used successors, will call for creation and distribution of a vast amount of cryptographic material, offering many lucrative targets for use of the new weapons of sabotage, possibly with the help of implanted agents. There is also the possibility that cryptographic secrets may be obtained by agents, as well as the more obvious danger of compromise by capture on the battlefield.
Considerable attention must be paid to the procedural rules that must be observed by all users and operators, and to the monitoring of their performance. The history of cryptology is full of cases in which a cipher system has been betrayed by carelessness or downright failure to obey operating instructions. This danger is aggravated by the fact that, in actual war, communications equipment is likely to be used for purposes that were not foreseen in the planning. Moreover the exact nature of future security problems is scenario-dependent, meaning that in system planning it is extremely important to study the scenarios that could materialize in the various potential trouble spots of the world.
Indeed the overall problem of achieving security for the type of communications facilities that will be best suited to combined arms operations in the 1980s and 1990s is extremely complex. But the problem should not be shirked. It calls for an interdisciplinary attack with full support from military thinkers as well as from experts in several specialized fields. And there must be strict secrecy, for, while we must attempt to anticipate all the tricks that might be used against us, we do not want to reveal whatever security measures we may be planning. In fact, in planning security measures, two fundamental objectives must be to keep the enemy in the dark as long as possible, and to be several steps ahead of him by planning systems so that they can be modified as necessary. Our planners should have been allowed to study how the Germans, following good cryptographic principles, did in fact introduce modifications in their Enigma machine and in their operating procedures. They added two new wheels not long before their invasion of Poland. They made a major change in operating procedures when they invaded France and the Netherlands. And they made several more changes later on.
Advanced planning of the kind we are discussing could be greatly helped by reforms in the present system of handling the security of day-to-day work. Picture a man who works for a government agency or military service, and who is responsible for deciding whether a particular item in a paper he is writing is to be classified secret, and what arrangements, if any, are to be made for downgrading its level of classification at some later date. His common sense may suggest that the information need not be classified secret at all, but he knows that if he is found guilty of a breach of security he may lose his job, or at least his prospects of promotion. A black mark of any kind on his record is something he desperately wants to avoid. From the human point of view one can hardly blame him if he decides to play it safe, slaps on a secret classification, and insists that there be no automatic downgrading of the classification level after stated periods of time. A decision on secrecy is by no means a simple problem. But it should not be determined by considerations of personal risk. It calls instead for a broad overall view and a specialist’s knowledge.
Current security procedures have an unfortunate side effect. A lengthy document, say of two hundred pages, containing information that could be valuable to many workers, is only too often classified secret because a few items appearing on a few pages are considered to deserve that classification. The result is that the whole document has to be subjected to the full security procedure. It must be stored in a locked cabinet and even its unclassified pages are frequently subject to restrictions on copying. This makes it unnecessarily difficult for researchers to obtain access to and quote from unclassified information of potential importance. One would think that a paper of this type could be issued in two parts—an unclassified major portion made available to all interested workers and a classified appendix made available under full security regulations to people qualified to know the few secret items.
There is also another side effect that is far from trivial. If some of the applications of a system of security regulations seem to be ridiculous, people may lose faith in the system as a whole, and it may become much harder than it need be to achieve strict obedience to regulations when it really matters. Indeed a general lack of respect for security procedures may produce more leaks of classified information than would otherwise occur.
In the advanced planning of systems that may develop from JTIDS, and particularly as concerns their cryptological aspects, very strict secrecy on many matters will be needed over long periods, but not forever. In many cases a time will come when a particular secret—for example, the cause of a system failure— should be made known because it will be helpful in advanced planning and in making people in general as aware as possible of what concerns their survival. With this in mind it would be well to provide for periodic review by competent authorities to determine when the release of secret information would be more beneficial than damaging—by no means an easy matter to resolve.
THE HUT 6 EXPERIENCE
In our thinking about future security measures we can draw lessons from the Hut 6 experience. Study of our records and those of the Central Party could be of real value in the advanced planning task of the early 1980s. Tom Belden, when he was lecturing at MITRE on the subject of crisis management, remarked that historical examples may give a truer picture of weaknesses than can be obtained from exercises, which tend to be artificial if not downright rigged. This remark has far deeper implications than I realized at the time. It applies also to scenarios. If we are to develop communications that will meet the needs of combat forces on future battlefields, we must think out many realistic scenarios, picturing situations that may arise. Of course our scenarios of future conflicts will try to take account of trends in military thinking and capabilities, but as Belden suggests, our dreamed-up scenarios may tend to be artificial or rigged. Why not think of wars of the past as scenarios against which bur advanced planning of communication can be tested? In this book I have been doing that in a negative way—examining past failures that must not be repeated—but a positive approach is also possible.
In thinking about communications systems that will meet the needs of future battlefields we must try to form a realistic picture of the messages that should flow through those systems. What information should the messages contain? Who will need what messages? How can one ensure that each combat element gets what it needs, and is not overloaded with information that it cannot absorb? One also has to worry about matters of internal security. Who is authorized to receive what messages, and how does this affect the arrangements for distributing cryptographic keys and other material? Answering questions such as these is, believe me, by no means easy. But, following up on Belden’s remark, why not find out what we can learn from the tactical messages that were passed, how they were distributed, and how internal security was handled in a real war?
I believe the Central Party that became part of the Hut 6 organization at Bletchley Park had more detailed knowledge of the entire communications system that handled Enigma traffic than anyone in Germany. It followed the movements, changes in control, retransmissions, the handling of different keys, and of course the chitchat that appeared in the logs. Leading members of the Central Party, given access to their old records, could no doubt piece together a very complete picture of a communications system that grew out of the realities of a wide-ranging war.
The Hut 6 decodes are another mine of still valuable information. Our breaking of Enigma keys was so extensive that the decodes would permit analysis of the types of messages that needed to be sent, the patterns of distribution, and the reasons for using so many different keys. Such an analysis, based on the firm foundation of real warfare, could provide a valuable background picture for our work on scenarios of future conflicts.
Here then—assuming that the wartime records of the Central Party, Hut 6, and Hut 3 have been preserved—we have a store of information meaningful to our advanced planning for future military communications and security procedures. This store, it seems to me, urgently needs to be opened up and studied. We cannot know precisely what we may bring to light; but we can be certain it will help us. If we do our studies well—and can manage to put the results to proper use—the spirits of Alastair Denniston and Edward Travis may well have reason to rejoice.
Bibliography
Books and Articles
BARAN, PAUL, On Distributed Communications, The RAND Corporation, Memorandum R.V1-3420-PR, August 1964. (Research sponsored by the United States Air Force under Project Rand—Contract No. AF49 (638]-700.)
BARNETT, CORRELLI, The Desert Generals, New York, Viking Press, 1961.
BAXTER, WILLIAM P., The Soviet Threat from the Sky, ARMY, April 1981.
BECKER, C, The Luftwaffe War Diaries, New York, Ballantine Books, 1969.
BELDEN, THOMAS G., Crisis Conferencing and the Pueblo Case, Institute for Defense Analysis (IDA). Systems Evaluation Division, February 1970.
CANBY, STEVEN, “NATO: More Shadow than Substance,” Foreign Policy Quarterly No. 8: National Affairs, Inc., 1972.
CANBY, STEVEN, “The Wasteful Ways of NATO,” IISS Survival, January/February 1973.
CAVE BROWN, ANTHONY, Bodyguard of Lies, New York, Harper & Row, 1975.
CLIFFE, TREVOR, Military Technology and the European Balance, IISS Adelphi Paper Number Eighty-Nine, 1972.
CONCEPTS DIVISION, AEROSPACE STUDIES INSTITUTE, AIR UNIVERSITY, Guerrilla Warfare and Air Power in Algeria, 1954-1960, Air University, Maxwell Air Force Base, Alabama, March 1965.
DIFFIE, WHITFIELD, and HELLMAN, MARTIN E., “New Directions in Cryptography,” IEEE Transactions on Information Theory, November 1976.
DIFFIE, WHITFIELD, and HELLMAN, MARTIN E., “Privacy and Authentication: An Introduction to Cryptography,” Proceedings of the IEEE, Vol. 67, No. 3, March 1979.
DONNELLY, C. L., “The Soviet Desant Concept,” RUSI Journal, December 1971.
ERICKSON, JOHN, Soviet Military Power, London, Royal “United Services Institute (RUSI), 1971.
ERICKSON, JOHN, “Shield-72: Warsaw Pact Military Exercises,” RUSI Journal, December 1972.
FALLOWS, JAMES, “America’s High-Tech Weaponry,” The Atlantic Monthly, May 1981.
FEHRENBACH, T. R., This Kind of War; A Study in Unpreparedness, New York, Macmillan, 1963.
FITZGERALD, PENELOPE, The Knox Brothers, New York, Macmillan, 1977.
FUTRELL, R. F., The United States Air Force in Korea, New York, Arno, 1971.
FUTRELL, R. F., Ideas, Concepts, Doctrines: A History of Basic Thinking in the United States AirForce, 1907-1964, Air University, Alabama, 1970.
GARLINSKI, JOZEF, The Enigma War, New York, Scribner, 1980.
GARTHOFF, R. L., Soviet Military Doctrine, Glencoe, Illinois, Free Press, 195 3.
GARTHOFF, R. L., The Soviet Image of Future War, Washington Public Affairs Press, 1959.
GUDERIAN, HEINZ, Panzer Leader, New York, Dutton, 1952.
HAMMETT, JACK C, JR., Tactical Communications—A Precious Resource, U.S. Army War College, June 1979.
HUNT, KENNETH, The Alliance and Europe: Part II: Defence with Fewer Men, IISS Adelphi Paper Number Ninety-Eight, 1973.
IEEE—INSTITUTE OF ELECTRICAL AND ELECTRONICS ENGINEERS, Publications: Proceedings, Spectrum, etc.
IEEE COMMUNICATIONS SOCIETY MAGAZINE: Special Issue on Communications Privacy, Vol. 16, No. 6, November 1978.
IEEE PROCEEDINGS, Special Issue on Packet Communication Networks, Vol. 66, No. 10, November 1978.
IISS—INTERNATIONAL INSTITUTE FOR STRATEGIC STUDIES, Publications: Adelphi Papers, Survival, The Military Balance, and Strategic Survey.
JONES, REG. V., The Wizard War, New York, Coward, McCann, St. Geoghegan, 1978.
KAHN, DAVID, The Codebreakers, New York, Macmillan, 1967.
KAHN, DAVID, Hitler’s Spies, New York, Macmillan, 1978.
KAHN, DAVID, “The Ultra Conference,” Cryptologia, January 1979.
KAHN, DAVID, “Cryptology Goes Public,” Foreign Affairs, Fall 1979.
KAHN, ROBERT E., GRONEMEYER, STEVEN A., BURCHFIEL, JERRY, and
KUNZELMAN, RONALD C, “Advances in Packet Radio Technology,” IEEE Proceedings. Vol. 60, No. 11, November 1978.
KEMENY, JOHN G., “An Extremely Small Malfunction (at Three Mile Island) and Then Something Terrible Happened,” Dartmouth Alumni Magazine, December 1979
KEMENY, JOHN G., “Saving American Democracy: The Lessons of Three Mile Island.” Technology Review, June-July 1980.
LEWIN, RONALD, ULTRA Goes to War, New York, McGraw-Hill, 1978.
LIDDELL HART, BASIL HENRY, The Remaking of Modern Armies, Boston, Little, Broun, 1928.
LIDDELL HART, BASIL HENRY, The German Generals Talk, New York, William Morrow, 1948.
LIND, WILLIAM S., “Some Doctrinal Questions for the United States Army,” Military Review. March 1977.
LUTTWAK, EDWARD N., “The American Style of Warfare and the Military Balance,” IISS Survival, March/April 1979.
LUTTWAK, EDWARD N., “Towards Rearming America,” IISS Survival, January/ February 1981.
MASTERMAN, JOHN C, The Double-Cross System, Yale University Press, 1972.
MELLENTHIN, F. W. von, Panzer Battles, Norman, University of Oklahoma Press, 1958.
MORSE, JOHN H., “Advanced Technology in Modern War,” A Lecture given at RUSI on November 26, 1975, RUSI Journal, June 1976.
PARKER, C. F., “Signals in the Sun,” Arizona Highways, June 1967.
PRESIDENT’S COMMISSION, JOHN G. KEMENY, CHAIRMAN, The Accident at Three Mile Island, U.S. Government Printing Office, October 1979.
RANDELL, BRIAN, Report on Colossus, Computing Laboratory, Newcastle University, England, 1976.
REDMOND, KENT C, and SMITH, THOMAS M., “Lessons from ‘PROJECT Whirlwind,'” IEEE Spectrum, October 1977.
RIDGWAY, MATTHEW B., The Korean War, New York, Doubleday, 1967.
ROBERTS, LAWRENCE G., “Data by the Packet,” Computer Report III, IEEE Spectrum,Computer Special, February 1974.
RUSI: Royal United Services Institute for Defence Studies (Whitehall, London, England), Regular Publication: The RUSI Quarterly Journal.
STENGERS, JEAN, “La Guerre des Messages Codes (1930-1945),” L’Histoire, No. 31, February 1981.
STEVENSON, WILLIAM, A Man Called Intrepid, New York, Harcourt, Brace, Jovanovich, 1976.
U.S. ARMY AIR FORCE, Condensed Analysis of the Ninth Air Force in the European Theater of Operations, with a Foreword by General Hoyt S. Vandenberg, 1946.
U.S. ARMY COMMAND AND GENERAL STAFF COLLEGE, “Readiness for the Little War,” Military Review, April-May 1957 editions.
WEYLAND, OTTO P., “The Air Campaign in Korea, “Air University Quarterly Review, Fall 1953.
WINTERBOTHAM, FREDERICK W., The ULTRA Secret, New York, Harper & Row, 1974.
WOODS, DAVID L., A History of Tactical Communications Techniques, Martin Company, Orlando, Florida, 1965.
